Introduction
Common Encryption Methods are important to understand in 2022. Today, the Internet provides essential communication and data sharing between billions of people. People use it as a tool for commerce, financial services, social interaction, and the exchange of vast amounts of personal and business information. With the growing popularity and increased internet use, security has become an exceedingly significant issue for every individual and organization.
Internet principles of openness and broad access are no longer a requisite when sending sensitive information over a public network. Unquestionably, you desire to keep confidential information from unauthorized access. Most importantly, you need to safeguard such data from cyber criminals with malicious intent. Undeniably, there are many aspects to security and many applications, ranging from secure card transactions to private data exchange and protection of healthcare information.
The most acceptable way out of this security problem is to alter the information so that only authorized people can read it. We are referring to encryption algorithms and methods, which we will address in this post.
But it is crucial to note that while information encryption is necessary for today’s secure communications, it is not by itself adequate. In effect, it would be best that you consider the encryption methods and algorithms discussed here as the first of the several measures for enhanced security posture in different IT environments and situations.
What is Encryption?
Computer encryption is based on the science of cryptography, which has been in use as long as humans have wanted to keep messages secret. Today, most forms of cryptography are computer-based since the traditional human-based encryption code is too easy for current computers to crack.
The Computer Security Resource Center (CSRC) defines encryption as the “cryptographic transformation of data (plaintext) into a form (ciphertext) that conceals the data’s original meaning to prevent it from being known or used.”
CSRC definition proceeds to define the reversal process. “If the transformation is reversible, the corresponding reversal process is called decryption, which is a transformation that restores encrypted data to its original state.”
Encryption Algorithms
The encryption process involves the use of algorithms. Perhaps you remember this from your algebra. An algorithm in mathematics refers to a procedure, a description of a set of steps that helps solve a mathematical computation. Today, algorithms are much more common and applicable in other areas than traditional mathematical procedures. They are applicable in many branches of science, including computer science and cybersecurity.
Within the content of cybersecurity, an encryption algorithm is a mathematical procedure that uses meaningless ciphertext to scramble and obscure a message. Cloudflare defines an encryption algorithm as the “method used to transform data into ciphertext.” The definition further states that an algorithm uses an encryption key to alter the data predictably. That way, users with the correct decryption key can turn the ciphertext back into plaintext.
Encryption vs. Cryptography
Frequently, cryptography is synonymous with encryption. However, cryptography is an umbrella term, with encryption as just one of the components. Cryptography refers to the study of techniques like encryption and decryption.
By definition, cryptography is the field of study of concepts like encryption and decryption used to provide secure communications. Conversely, encryption is more of a mathematical operation or algorithm for encoding a message. Therefore, cryptography, being a field of study, has broader categories and ranges, while encryption is just one technique, which forms one aspect of cryptography.
Gary C. Kessler, Professor of Cybersecurity and Chair of the Security Studies and International Affairs Dept. Embry-Riddle Aeronautical University, lists five main functions of cryptography:
- Privacy and confidentiality: ensuring that no one can read the message except the intended receiver
- Authentication: the process of proving one’s identity
- Integrity: assuring the receiver that the received message has not been altered in any way from the original
- Non-repudiation: a mechanism to prove that the sender really sent a specific message
- Key exchange: the method by which crypto keys are shared between sender and receiver
Cryptography is a process that starts with unencrypted data or plaintext. You employ encryption algorithms to encrypt the data into ciphertext, which will, in turn, be decrypted back into readable and usable plaintext.
Common Encryption Methods
There are two main types of common encryption methods – symmetric and asymmetric encryption.
1. Symmetric Encryption
Symmetric encryption is also known as private key encryption. Kessler and other researchers refer to this method as Secret Key Cryptography. As the name implies, both the sender and receiver use only one key in this encryption method. Symmetric cryptography has a considerable advantage over the asymmetric algorithm when it comes to speed. This method is faster to run in terms of encryption and decryption processes since it uses one key, which is much shorter than in asymmetric encryption techniques.
Even though symmetric encryption offers speed, the method carries a high risk around key transmission. Notably, symmetric cryptography uses the same key to encrypt messages, and the sender must share it with the recipients for the decryption process. Every time users share the key, the risk of interception by hackers increases.
What are the popular uses of symmetric encryption? Organizations can use this encryption method for bulk data transfer due to its speed. Besides, this encryption method is useful for encrypting data stored on a device when there is no intention to transfer it. Symmetric encryption is used in the banking sector for payment applications, specifically card transactions, where personally identifiable information (PII) must be protected to prevent identity theft.
2. Asymmetric Encryption
Asymmetric encryption, alias public-key encryption, is different from symmetric since it uses two keys, one public (anyone can access) to encrypt information and a private key to decrypt data. Typically, it is easy to compute the public key from the private key but highly complicated to generate a private key from the public key. Asymmetric encryption has slow speeds, making it far less efficient for bulk operations.
Asymmetric encryption offers enhanced security since it uses two different keys. A post on Venafi states that public-key cryptography is used as a “method of assuring the confidentiality, authenticity, and non-repudiation of electronic communications and data storage.”
Therefore, the method is mainly used in tasks where security is prioritized over speed. Typical applications of asymmetric encryption include digital signatures to confirm user identities. When accessing a website on the public cloud, it becomes complicated, and symmetric encryption does not work since you do not control the other end of the connection. This activity requires you to share a secret code with other entities without the risk of intruders on the Internet intercepting it in the middle.
Let us now turn our attention to the widely used encryption algorithms.
Common Encryption Algorithms
There are several common encryption methods in use today. We cover ten popular algorithms in this post.
1. Triple-DES (3DES)
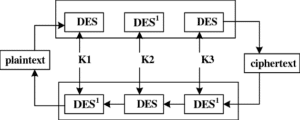
Triple DES applies the older Data Encryption System (DES) algorithm three times to the same block of text. 3DES falls under the symmetric encryption that uses the block cipher method.
A block cipher refers to a scheme that encrypts one fixed-size block of data at a time. In a block cipher, a given plaintext block will always encrypt to the same ciphertext when using the same key, which Kessler refers to as deterministic. In contrast, the same plaintext will encrypt to different ciphertexts in a stream cipher.
The 56-bit DES algorithm, one of the most well-known and well-studied secret-key cryptography, was inadequate from the get-go simply because it is too short. As a result, it was gradually vulnerable to brute force attacks as computational power increased. Designedly, 3DES applies the DES algorithm thrice to each data block. In effect, the revised algorithm gets a total length of up to 168 bits. Kessler writes that 3DES became an interim replacement to DES in the late 1990s and early 2000s.
The enhancements make it efficient for various uses, including securing credit card transactions in electronic payment industries and other financial services. Microsoft’s Outlook, OneNote, and System Center Configuration Manager 2012 also use Triple DES to protect user content and system information.
2. RSA

RSA (Rivest-Shamir-Adleman in full) is an asymmetric encryption algorithm often associated with the Diffie-Hellman key exchange method discussed in the next section. This encryption algorithm creates the modulus using two prime numbers, which then generate the public and private keys.
RSA encryption strength increases exponentially with the increase in key size, which is typically 1024 or 2048 bits long. Typically, RSA implementation is combined with some sort of padding scheme to prevent messages from producing insecure ciphertexts.
Since no active patent governs RSA, anyone can use it. Mainly, the algorithm performs encryption, decryption, and signature verification, all with the same two functions. Based on its security capabilities, RSA asymmetric technique is the standard for encrypting data sent over the Internet.
But RSA has some shortcomings – the algorithm is slow due to its very nature of using public-key cryptography for encryption.
3. Diffie-Hellman

Diffie-Hellman encryption algorithm, also known as Exponential Key Exchange, is a public key exchange method used to share private keys across public networks. One of the common encryption methods, sometimes the algorithm acts as a key agreement protocol that determines the private key used by both parties in data exchanges.
Diffie-Hellman has been in use for decades, mainly for sharing private keys in symmetric encryption applications. It allows two entities with no prior knowledge of each other to jointly establish a shared secret key over the Internet or an insecure channel.
However, the Diffie-Hellman algorithm lacks authentication. Data using this encryption technique are vulnerable to man-in-the-middle attacks. Diffie-Hellman is well suited for data communication but less often used for data stored or archived for a long time.
Due to its nature, the Diffie-Hellman public domain algorithm allows you to secure a wide range of internet services. Additionally, the algorithm provides the basis for multiple authenticated protocols. A case in point is Diffie-Hellman’s application in forward secrecy in Transport Layer Security’s (TLS) ephemeral modes.
4. ElGamal Encryption
ElGamal encryption is another asymmetric key cryptography based on the Diffie-Hellman Key Exchange. The algorithm’s security depends on the difficulty of computing discrete logs in a large prime modulus. In the ElGamal technique, the same plaintext produces a different ciphertext every time it is encrypted. The algorithm produces ciphertext that is twice as long as the plaintext.
ElGamal encryption can be defined over any cyclic group. Its security depends on the properties of the underlying group as well as the padding scheme applied on the plaintext.
The encryption technique is used in the recent Pretty Good Privacy (PGP) versions and GNU Privacy Guard. Besides that, ElGamal encryption is used in a hybrid cryptosystem, where the symmetric cryptosystem encrypts the plaintext, then the system deploys ElGamal to encrypt the key.
5. Blowfish
Much like Triple DES, Blowfish is another symmetric key algorithm designed to replace DES. This common encryption method is famous for its speed and effectiveness. Since it is placed in the public domain, anyone can use the Blowfish algorithm for free.
Blowfish works with a 64-bit block length. Besides, it has a variable key size ranging from 32 to 448 bits. Encryption in Blowfish algorithm involves 16-round Feistel cipher, using large key-dependent S-boxes.
One drawback of the Blowfish algorithm is that it is vulnerable to birthday attacks, especially in contexts like HTTPS. Apart from that, it is apparent that Blowfish is ineffective in encrypting files larger than 4 GB due to its small 64-bit block size.
What are some of the popular Blowfish uses? You can find the encryption algorithm in various software categories, specifically database security, eCommerce platforms, file and disk encryption, and archiving tools. Blowfish is also efficient in password management, file transfer, secure shell, steganography, and email encryption.
6. Twofish
Bruce Schneier created the Twofish symmetric cipher algorithm to replace the less secure Blowfish algorithm. Twofish used the Situation Box (S-box) as part of its encryption method. Twofish uses a 128-bit block size and supports a key size of up to 256 bits, making it secure from brute force attacks. One-half of the n-bit key represents the encryption key, while the second half modifies the encryption algorithm.
Twofish is slightly slower than AES but comparatively faster for 256-bit keys. On top of that, the algorithm is flexible, making it ideal for use in network apps where keys change frequently. Moreover, Twofish is efficient in systems where only a small amount of RAM and ROM is available for use. More frequently, the algorithm comes bundled in encryption tools like TrueCrypt, GPG, and PhotoEncrypt.
7. AES

The Advanced Encryption Standard (AES) is the successor of DES. NIST initiated a public four-and-a-half-year process to develop a new secure cryptosystem for U.S. government applications in 1997. This development opposed the very closed process in the adoption of DES more than two decades earlier. The result of the process was AES, which became the official DES successor in December 2001.
AES algorithm is a block cipher that features three sizes: AES-128, AES-192, and AES-256. AES encryption algorithm puts data into an array before performing a series of transformations known as rounds. Essentially, AES is exceptionally efficient in 128-bit form. It can also leverage 192 and 256-bits keys for heavy security. It operates ten rounds for 128-bit keys and 12 rounds for 192-bit keys. The 235-bit key has 14 rounds. Also, the algorithm uses secret-key cryptography known as Rijndael, a block cipher designed by Belgian cryptographers Joan Daemen and Vincent Rijmen.
By design, the AES algorithm is sufficient to protect government secrets and sensitive corporate information. It is naturally secure, and security analysts have not discovered any practical attacks against the algorithm. Accordingly, the encryption algorithm has become a trusted standard for the United States Government and various organizations.
Notably, AES has low RAM requirements and high speed, qualifying it as the preferred algorithm to hide top-secret information. Also, the algorithm can perform optimally on an array of hardware, ranging from 8-bit smart cards to high-performance processors. AES is also deployed in many different transmission technologies and protocols, such as WPA2 protection for Wi-Fi networks, voice over IP technology (VoIP), and signaling data.
8. IDEA
The International Data Encryption Algorithm (IDEA) uses a 128-bit key. IDEA is like AES since it works on a system of rounds. Users have deployed the block cipher for an email privacy technology referred to as Pretty Good Privacy (PGP), where data is transmitted in 64-bit blocks.
IDEA divides the 64-bits block into four portions of 16 bits each. Next, the sub-blocks are transformed individually in each round. IDEA leverages substitution and transposition to scramble data.
9. RC6
RC6 is also a symmetric-key block cipher algorithm. However, RC6 has a slight twist since it runs blocks of variable length. Besides, the rounds that the data undergoes during transformations are variable.
RC6 can handle blocks of 128 bits, with a key size that can range between 0 and 2040 bits.
Undoubtedly, RC6 is an improvement on previous RC4 and RC5 algorithms. What’s more, RC6 is parameterized, meaning it adds an extra complexity layer to encryption.
10. Elliptic Curve Cryptography
Elliptic Curve Cryptography (ECC) is an asymmetric encryption method based on the elliptic curves’ algebraic structure. Instead of following the conventional approach of generating keys as the product of large prime numbers, this common encryption method creates keys through the elliptic curve equation property.
The elliptic curve size determines the difficulty level of the problem. It can provide a level of security with a 164-bit key that other systems like RSA require a 1024-bit key to achieve.
Typically, ECC is applicable for key agreements, pseudo-random generators, and digital signatures. Researchers are developing ECC as the successor to the popular RSA approach. NSA has dramatically supported the algorithm, and it has expressed the intention to deploy Elliptic Curve Diffie-Hellman for key exchange and Elliptic Curve Digital Signature algorithm for digital signature.
Conclusion
We cannot overemphasize the importance of encoding data to keep it hidden and inaccessible to unauthorized users. With the frequent and sophisticated cyberattacks organizations experience today, encryption helps protect private information and sensitive data. Apart from cyberattacks, machine’s computation power is constantly evolving, so security experts must innovate new approaches to keep attackers at bay.
Various encryption techniques and algorithms enhance the security of communications between client apps and servers. Encryption algorithms are mathematical processes that turn plaintext into unreadable ciphertext. In essence, when you use the appropriate algorithm to encrypt data, even if an intruder gains access to it, they will not be able to read it.
We have established that some common encryption methods are more robust and more reliable than others. In some cases, new algorithms emerge in response to calls to replace existing but weaker ones. For instance, 3DES and AES improved on the shortcomings of DES. That way, older algorithms became obsolete, while others were revised into newer robust versions. This post features reliable encryption algorithms that defend information from the relentless ambush of cyberattacks. Unquestionably, the Internet and its uses would not be possible without fitting encryption schemes and algorithms.
