Introduction to Computer Forensics
Computer Forensics is used to answer two of the most commonly asked questions about hacking attempts and data breaches:
- How did the attack happen?
- Is there a possibility of recurrence, and can such threats be prevented from ever happening again in the future?
There are no specific answers to these questions as it depends on the level of severity or rather the complexity of the cyber-attack. The process of identifying how the attack happened and whether it can happen again in the future can take weeks or even months. For an in-depth analysis of the origin of the threat, several penetration tests have to be carried out through a systematic approach.
In this regard, several lines of defense have to implemented to push the underlaid defense mechanism to their full breaking point. This is done by a tech expert to identify any hidden vulnerabilities within a system. Appropriate lines of codes have to be used to detect the threat. This is where the role of forensics comes into play. The analysis might start by examining any evidence left behind by the attacker. Any proof or remnant of the cyber-attack should be collected and carefully examined for any lead. It is from the findings that the forensics examiners and investigators can now answer questions such as “who initiated the attack? What leads to the attack? Where did the threat come from? When was the attack launched? And why was the system attacked?”.
As we get deeper into the study, it is essential to keep in mind that the field of computer forensics as it relates to information technology is vast. It involves many minor branches of specialties. Some of these sub-specialties include database forensics, digital forensics, logical access forensics, mobile forensics, to name a few.
In this article, we provide an overview or a brief introduction into the field of computer forensics by primarily focusing on what it is all about, what drives the need for computer forensics, steps on how to conduct detailed forensics, and other details that encompass computer forensics.
The Need for Computer Forensics
The world has become a global village with the advent of the internet, digital life, and computer systems. Life might seem impossible without these technologies as they are elemental to everything we do. Information and other valuable data can be stored or transferred by electric devices such as thumb drives, internet, laptops, and other methods. Diverse variation and development of information storage and transfer capabilities have facilitated the development of forensic techniques, procedures, investigators, and forensics tools.
In the recent past, we have witnessed and experienced a tremendous increase in crime rates involving computer use. Governments, large corporates, small business enterprises (SBE’s), and individuals are targets for malicious hackers who aim at stealing any valuable information they can prey easily access. The attack leads to massive financial loss in most cases. As a result, computer forensics’ in conjunction with a digital investigation, have merged as a proper channel to identify, collect, examine, analyze, and mitigate or report the given computer crimes.
What is Computer Forensics?
Computer forensics is a combination of two terms: forensics, which refers to the scientific techniques or tests carried out in an attempt to detect a cyber-threat and computer, which is the medium used to convey data or information. In past studies, some scholars have defined forensics as the process of applying scientific techniques and skills during identification, examination, collection, and report of cyber-crime to the court. Dr. H. B Wolfe defined computer forensics’ as “a methodical series of techniques and procedures for gathering evidence, from computing equipment and various storage devices and digital media that can be represented in a court of law in a coherent and meaningful format.” The term forensics, as defined by Wolf, implies that forensics is a process that involves analysis and presentation of data collected. However, all types of data that can be used as evidence is critical.
A formal definition of computer forensics is as follows:
“It is the discipline that combines the elements of law and computer science to collect and analyze data from computer systems, networks, wireless communications and storage devices in a way that is admissible as evidence in a court of law.”
Motivations behind an attack
What data should you seek as an investigator?
After an occurrence of cyber-attack, collecting all relevant evidence is of utmost significance in responding appropriately to the questions which were outlined above. A forensic examiner or investigator is primarily concerned with a specific piece of evidence, which is known as “latent data.”
Latent data is also known as ambient data. In the cybersecurity world, ambient data is a type of data that is not easily accessible or visible at first glance at the scene of a Cyber-attack. In simple terms, latent data requires an extra mile from a security expert for it to be accessed as significant evidence. An expert has to engage themselves in much more in-depth investigations to unearth this type of data. Ambient data has many uses to it, and it is equally important just like other types of data except that it is implemented such that access to it has been minimal.
Examples of ambient data include the following;
- Information that cannot be readily viewed by the commonly used software applications
- Information or data that cannot be readily read by the operating system in place.
- The information which is present in computer storage but not readily referenced in the file allocation tables
- Previously deleted data stored in:
-
- Swap files
- Memory dumps
- Blank folders in the hard drive
- Print spooler files
- Slack space between the existing files and the temporary cache.
Importance of computer forensics
To a business or corporation, in-depth forensics is paramount. For instance, there is a misleading assumption that implementing defense with routers, firewalls, antiviruses, etc. is sufficient and reliable enough to thwart off any cyber-attack. With the highly versatile technology which is subject to rapid advancements, a security professional should be aware that planting only firewalls as their defense line cannot prevent hackers from accessing their system.
From a computer forensics point of view, the assumption is untrue since measures such as firewalls only give a scratch of the needed information in case of an attack. These specialized pieces of software can only provide information to a certain degree. Such a mechanism does not possess the deeper layer of data required to provide clues on what happened. To source these specific details, an organization is forced to implement security mechanisms along with the software mentioned above. Deploying this type of security model is known as “Defense in Depth.”
In systems where defense in depth model is applied, there is a higher possibility that the data presented in case of an attack can be readily admissible in a court of law. After this, the perpetrators who launched the attack can face justice.
Also, an enterprise or corporation can meet the legal requirements such as HIPPA by incorporating the tenets of a defense in depth. Federal mandates and legislations require that every type of data is stored and archived appropriately for auditing. An entity can suffer severe financial penalties for failing to meet the compliance measures put in place.
Computer Forensics Process
While conducting forensics, it is vital to maintain a chain of custody of the evidence and latent data throughout the investigation. Therefore, take note that the steps outlined below are only general guidelines on how to conduct computer forensics in case of an attack. The specific sequencing of activities can vary depending on the nature of the threat. It is recommended to implement a dynamic method for forensic as each cyber-attack is unique.
Work procedure can be sub-dived into five major categories:
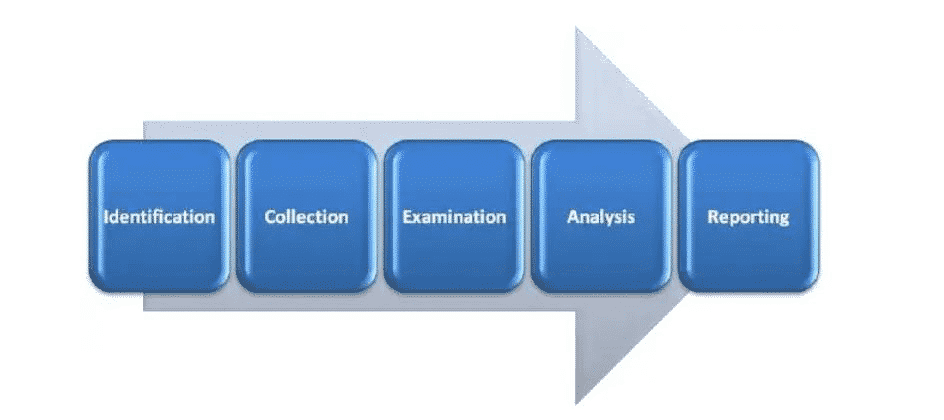
Identification
This initial step in computer forensics is to understand and identify the scenario. This is where the investigator points out the specific reason for conducting forensic analysis. The investigator also identifies the nature of the incident, the parties involved, and the resources required to satisfy the needs of the case.
Collection
The collection of data is the most critical step in this chain of custody because the entire analysis is primarily dependent on the collected data as evidence from the crime scene. Collection is defined as the process of data acquisition while maintaining the transparency or integrity of the data.
Timely execution of the collection process is key to maintaining the integrity and confidentiality of the data collected. This is because essential data such as latent data may get lost if not acted upon promptly.
Evidence
In this third step, the collected data is examined by following standard techniques, methodologies, tools, and procedures to extract meaningful information related to the case.
Analysis
Since all the five steps are linked, analysis is the step where data analysis of the examined data is conducted. The investigator has the task of finding any evidence against the suspect. The techniques and tools should be legally justified as it helps to create and present the report to a court of law.
Reporting
This is the final and perhaps the most critical step. Here, the investigator is expected to logically document the process used to collect, examine, and analyze data. It also entails how the tools and procedures were selected. The primary aim of this step is to report and present the findings justified by the evidence.
The above five steps can be subdivided into several smaller parts, where every subcategory has standard operating procedures that are specific to them.
Computer Forensics Team
The Forensics Team is expected to follow a given structure while executing their documentation process. The contents of their documents are required to be preserved, verified, and appropriately documented. A forensic team must have in-depth know-how of every investigation. This should be right from the beginning of the project and should cut through the scope, dimensions, and the various methods used for the investigation process. The methods used should be proper and legal such as the legal obtaining and collection of proper bit-stream “hash encrypted” copies of evidence. The linear nature of investigation should be primarily based on proper documentation and concrete supporting evidence to avoid unexpected results that technology might yield.
In addition to law enforcement and security firms, every organization should develop the capacity to solve their basic issues and investigations internally. In the case where it is not possible to form a competent investigative team within the organization, then you can hire experts from small computer investigation firms to aid with investigations. An organization can also create their own investigative firm to supply computer forensic services. To do so, the following key people form part of your investigation team.
Investigators
This is a group of individuals who tackle and solve the case. The size or number depends entirely on the size of the firm. They are mandated with the task to apply techniques and use relevant techniques to find tangible evidence against the suspected intruder. They can work parallel with law enforcement agencies as they are expected to act promptly upon the occurrence of a suspicious activity, which may lead to an attack.
Photographer
He or she is vital for recording events as they unfold during the investigations. Their job is to take photographs.
Incident Handlers or the first respondents
The primary role of incident handlers is to monitor and act upon the occurrence of any computer security incidence. They check for malicious activities such as those related to breaching network policy, hijacking of server, RAT, installation of malicious codes or injection of code.
IT engineers and technicians
This group is responsible for the day-to-day operation of the firm. They are technicians and engineers to manage the forensics lab. It should consist of IT support, desktop support personnel, network administrator, and security engineers.
The key roles of this personnel are to ensure flawless operation of organizational functions, maintain the required back up, troubleshoot for any problem, and continuously monitor the system.
Attorney
The whole essence of carrying out the investigations is to document and finally report the issue to a court of law, implying that the presence of an attorney as part of your firm is mandatory.
Computer forensics rules
Below is a list of some of the rules that should be kept in mind while conducting an investigation.
1. Eliminate every possibility of investigating the original evidence
Produce several exact copies of the initially collected evidence to reduce the chances of examining the original. Create duplicates; this is the first and the most fundamental of all the rules and should be prioritized first before carrying out any further investigations. Make the exact copies of the original to maintain the integrity of the outcome.
2. Only proceed if it is within your knowledge.
In the case where you stumble on a roadblock while conducting investigations, only proceed if you can understand the solution from your knowledge or experience. You can consult from other experienced guides to get help with that particular issue. This is to protect data from any damage. Do not take the task as a challenge, but rather as an opportunity to learn and enhance your expertise level.
3. Stick to boundaries and rules of evidence
The rule of evidence must be adhered to for the given data to be valid as evidence in court.
1. Document
Record the behavior and any changes that may occur to the evidence. An investigator is expected to document the result, nature, and the reasons why the transition occurred with the evidence. For instance, rebooting a machine may lead to alterations in its temporary files, and an investigator should note this.
2. Abide with the legal authorities
Before the onset of any investigation activity, ensure that you acquire written permission on the details and scope of your investigation. During the investigation, several duplicates and copies must be produced, and without an official or legally written permission, then this would be termed as a breach of IT security policy.
3. Prepare to testify
After completing the documentation, the evidence is taken to court. You should make yourself prepared to testify in court so as not to lose the case.
4. Use a traceable path
Your method should be trackable. Avoid trial and error methods. Trial and error methods are not convincible. Ensure to note down each step and be consistent in your actions.
5. Be efficient
Be efficient in minimizing the chances of data loss. Some data, such as latent data, are highly volatile and may quickly disappear if not collected in time. Artificial intelligence can be used to speed up the process but do not end up in a rush situation. The human workforce should increase as necessary. And as a rule, always start with volatile data as you collect evidence.
6. Do not quit before collecting evidence
Investigations cannot proceed without data to use as evidence. Hence you should not shut down the system before collecting all the evidence. Also, shutdown or rebooting of the system leads to loss of volatile data, so avoid this at all costs.
7. No running programs on the attacked system
Running a different program may trigger another program or activity within the system, which may lead to unbearable consequences.
Types of evidence
Evidence is the primary support for a claim in court. It can be classified using many types of different characteristics. Below is a look into some of the four major types of evidence;
1. Real/tangible evidence: As the name suggests, real evidence consists of tangible/physical material e.g., hard-drive, flash drive, etc. Apart from the material, a human also might be real evidence, e.g. an eye witness.
2. Original evidence: This is the evidence of a statement made by a person other than the testifying witness. It is offered to prove that the statement was made rather than to prove its truth. This is generally an out of court statement.
3. Hearsay evidence: It is also referred to as out of court statement. It is made in court, to prove the truth of the matter declared.
4. Testimony: When a witness takes oath in a court and give his/her statement in front of the court. Evidence should be admissible, accurate, and authentic; otherwise, it can be challenged while presenting the case in the court.
Conclusion
This is the end of this mini-course, but certainly not the end of knowledge and skills. Technology is rapidly changing with time. With the presence of several storage media, it is an individual, organization, or institution’s effort to understand the media so as investigate whenever needed. While conducting forensics, maintain the highest level of integrity at every stage as much as possible as it is crucial for the success of the investigations.