Business email compromise (BEC) or email account compromise (EAC) are a huge concern for most of the organizations these days. These attacks are designed to trick people into thinking that the email that they are receiving is from a person belonging to a senior position such as the Chief financial officer, CEO or a partner in the organization. The email is forged with the content that requests the employees to wire money to fraudulent locations. It can be in the form of:
- Fake name in the ‘From’: The ‘From’ field in the email consists of the spoofed name of the executive.
- Incorrect ‘Reply-to’: Here, attackers use the real name and email address of the impersonated person. However, the ‘reply-to’ field consists the email address of attacker.
- ‘Reply-to’ is missing: The name and the email address belongs to the impersonated executive. However, there is no email address in the ‘reply-to’ thus making it difficult to communicate with the ‘executive’.
- Identical Domain: Here, attacker not only impersonates the executive but also, uses a ‘From’ address that is identical to the original one.
In the year 2013, BEC scams began with hacking or spoofing of email accounts of chief financial officers or chief executive officers. Fraudulent emails requesting wire payments to fraudulent locations were sent to employees. BEC attacks result in the compromise of personal emails, vendor emails, spoofed lawyer email accounts. It can be in the form of:
- Bogus Invoice: In this type of BEC attack, attackers pretend to be the suppliers requesting for fund transfers as payments to an account owned by fraudsters.
- CEO Fraud: Attackers pose as the CEO or any executive and send an email to employees in finance, requesting them to transfer money to the account they control.
- Account Compromise: A high-level employee’s email account is hacked and used to request invoice payments to vendors listed in their email contacts. Payments are sent to fraudulent accounts.
- Attorney Impersonation: Attackers pretend to be a lawyer or from the law firm who oversees crucial and confidential matters.
- Data Theft: Employees under HR or bookkeeping are targeted to obtain personally identifiable information (PII) of employees and executives to be used for future attacks.
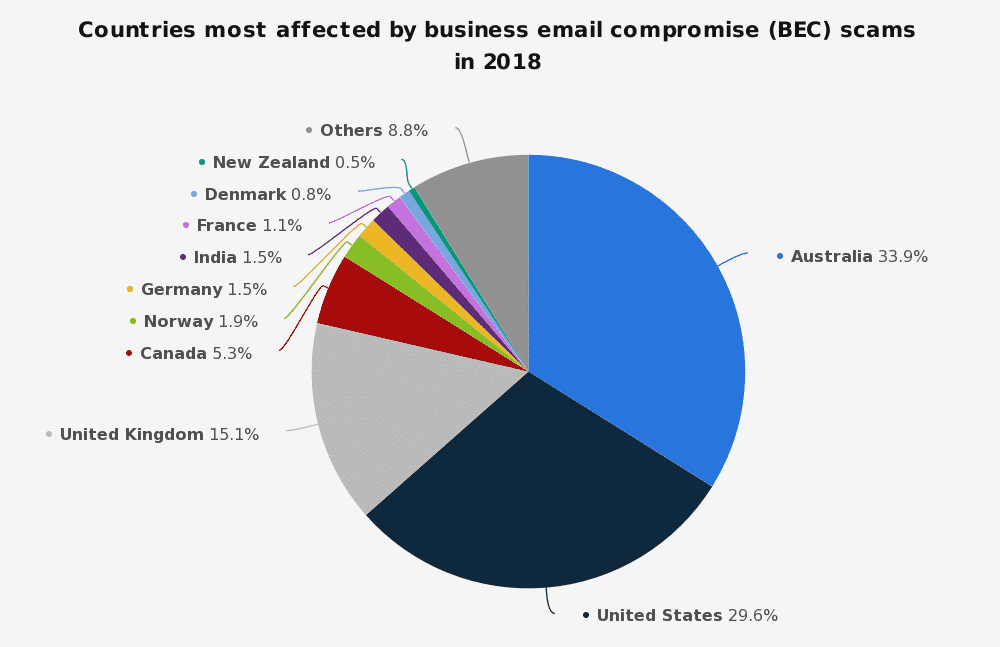
Source: Statista
The market for BEC attacks has expanded very fast within a period of few years. According to FBI’s latest report on BEC frauds, losses due to BEC scams have reached $12.5 Billion worldwide. Between October 2013 and December 2016, financial losses due to BEC had cost organizations $5.3 billion globally. In May 2018, the FBI’s Internet Crime Report indicated more than $675 million losses due to BEC in the year 2017. Complaints related to BEC rose up to 351,937 with a 14.3% increase from the year 2017 to 2018. Losses due to BEC attacks increased by 90.8% from $1,418.7 million to $2,706.4 million during 2018.
So, why are BEC attacks so popular?
Unlike phishing or ransomware attack, there are no malicious URLs or attachments in these emails. BEC is a form of social engineering attack that is designed to psychologically trick employees with the help of impersonated identities that are already known to them. This includes ordering employees to perform their daily tasks or sending emails that are written in an authoritative manner thus, making it difficult for victims to question the legitimacy of the email and follow what is being narrated to them via forged email. In short, attackers do not have to put in much effort other than using their brains to manipulate victims.
With this emerging trend of deploying BEC attacks, it becomes extremely important to employ security measures to safeguard your organization and its employees against such cyber-threats.
How can you protect your organization against BEC attacks?
Limited authority: It is imported limit the authority to people who check payments and those who approve or process wire transfer.
Train your employees: One of the effective ways of safeguarding against BEC attacks is by providing cyber awareness training. The training helps employees in gaining awareness about BEC attack as well as about the methodologies and strategies used by attackers to trick them.
Policy-based protection: This can be considered as the most effective preventive measure against BEC attacks. This helps in examining the sender reputation and sender-recipient relationship that can detect different forms and types of BEC attacks. Policy or authentication-based protection helps in authenticating your email domain. With the help of SPF and DKIM, the authenticity of an email can be easily established. SPF is an email authentication technology that specifies the sender who can send an email on domain’s behalf. DKIM allows the transmission of an email in a manner that it can be verified by the email provider. A more powerful authentication tool is DMARC that adds on to the protection provided by SPF and DKIM.
Setting up DMARC policy helps in allowing sender to indicate that their email is protected by either DKIM and SPF or both. DMARC records consists of these policies and helps in defining DMARC rulesets. It ensures that spoofed emails are not delivered to your email domain. With the help of products such as KDMARC, DMARC records can be generated and analysed for effective protection of the email domain.
The main source of communication within an organization is email. Conducting businesses, sending proposals, major decisions and deal closure are all done through emails. It is, therefore, extremely important to secure your email domain by implementing security measures that can effectively block malicious emails.