How cybercriminals plan attacks is a basic question that every cybersecurity expert needs to know. Cybercriminals use various tools and techniques to identify the vulnerabilities of their target victims. The target can either be an individual or an organization. Most cyber-attacks aim at stealing valuable information or breaching systems. Criminals plan active and passive attacks.
Active attacks actively aim to alter the targeted system. On the other hand, passive attacks only attempt to acquire as much information as possible about their target.
Active attacks may affect the integrity, authenticity, and availability of data, whereas passive attacks lead to breaches of privacy.
Cyber-attacks can also be classified as either outside attacks or inside attacks. An attack originating or executed from within the security perimeter of an organization is called an inside attack. In most cases, inside attacks are engineered and performed by employees who have access to the organization’s credentials and knowledge of the organization’s security infrastructure.
However, attacks executed from outside an organization’s or entity’s security firewall are referred to as an outside attack. This type of attack is performed by someone that does not have a direct association with the organization. The attack can be made over the internet or via a remote access connection.
In this article, I’ll walk you through many concepts so that you clearly understand how the mind of a cybercriminal works and the exact thought process of how they plan cyber-attacks. I will cover topics including types of hackers, attack techniques, types of cyber-crime, attack thought processes, how cyber criminals choose their target. I will also explain other relevant areas that will give you an in-depth understanding of a cybercriminal’s mind frame or instead thought process.
Who are cybercriminals?
Most cyber-attacks are spearheaded by individuals or small groups of hackers. However, sizeable organized crime also exploits the internet. These criminals, branded as “professional” hackers, develop new and innovative ways to commit crimes. Others form global criminal conglomerates and treat cyber-crime like an income-generating investment.
Criminal communities operate as a unit, where they share strategies and tools to launch coordinated attacks, either from the same place or from different remote locations. The “business” has advanced over the past few years with the emergence of underworld cyber-markets, where you can conveniently purchase and sell stolen credentials and other information of significance.
The internet makes it very difficult to track down cybercriminals. It allows cybercriminals to collaborate anonymously. Attacks can be launched and controlled from any location across the globe. Hackers often use computers that have already been hacked, and any form of identity is removed.
This makes it extremely difficult to identify the attacker, tool, or gadget used to execute the attack. Crime laws vary from country to country, making the situation very complicated when an attack is launched from a different country.
Types of Cyber Crime
1. Cyber-crime targeting an individual
In this type of attack, criminals exploit human weaknesses such as innocence, ignorance, and avidity. Attacks targeting an individual include copyright violation, sale of stolen or non-existent properties, financial frauds, harassment, etc. The latest technological advancements and developments of new innovative attacking tools allow cyber criminals to expand the group of potential victims.
79% of security professionals think that the biggest threat to endpoint security is the negligence among the employees for security practices. We are all human, and we all make mistakes. However, many people are scheming day and night to take advantage of a single silly mistake. This mistake can cost you tremendous financial loss.
2. Cybercrime against an organization
Cyber-attacks against an organization are also referred to as cyber terrorism. Hackers rely on computers and the internet to perform cyber terrorism, steal confidential information or destroy valuable files, take total control of the network system, or damage programs. An example is a cyber-attack on financial institutions such as banks.
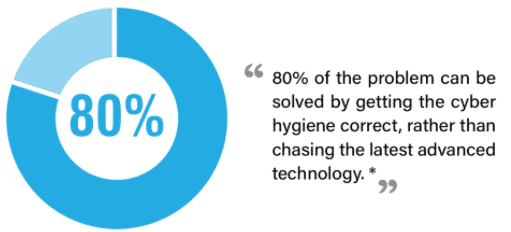
3. Cybercrimes target valuable assets
This kind of crime involves stealing property such as laptops, pen drives, DVDs, mobile devices, CDs, iPad, etc. In some cases, an attacker may infect the devices with a malicious program such as malware or Trojan to disrupt the functionality. One of the Trojans used to steal information from target victims is known as a Shortcut virus. The Shortcut virus is a form of a virus that converts your valid files into a form that cannot be accessed on your PC’s hard drive or Flash drive. The shortcut does not delete the actual file but instead hides it behind the shortcut files.
4. Attacks using a single event
From the victim’s point of view, this attack is performed with a single action. For example, an individual mistakenly opens an email containing corrupted files, which may either be malware or a link that redirects you to a corrupted website. An attacker then uses the malware as a backdoor to access your system and take over the control of the entire system if need be. This type of attack can also be used to cause organization-wide havoc, and it all starts with a single click by an “ignorant” employee.
5. Cyber-attacks considering a chain of events
In some situations, hackers perform a series of events to track a victim and interact with them personally. For example, an attacker may make a phone call or chat room to establish a connection with the victim and afterward steal or explore valuable data by breaching the relationship between the two parties. Nowadays, this type of attack is prevalent. Therefore, you should be extremely cautious before accepting a friend request on Facebook or joining a WhatsApp group using links from unknown sources or WhatsApp groups.
How Cybercriminals Plan Attacks
Below are the three phases involved in planning a cyber-attack.
- Reconnaissance – this is the information gathering stage and is usually considered a passive attack.
- Scanning and scrutinization of the collected data for validation and accurate identification of existing vulnerabilities.
- Launching the attack – entails gaining and maintaining access to the system.
1. Reconnaissance
The first step in how cybercriminals plan attacks is always Reconnaissance. The literal meaning of reconnaissance is an act of exploring with an aim or goal of finding someone or something about the target. Concerning cybersecurity, it’s an exploration to gain information about an enemy or a potential enemy. In cybersecurity, reconnaissance begins with “Footprinting”, the initial preparation towards the preattack phase, and entails collecting data about the target’s computer infrastructure as well as their cyber-environment.
Footprinting gives an overview of the victim’s weak points and suggestions on how they can be exploited. The primary objective of this phase is to provide the attacker with an understanding of the victim’s system infrastructure, the networking ports and services, and any other aspect of security required for launching attacks.
Thus, an attacker attempts to source data from two different phases: passive and active attacks.
2. Passive attacks
This is the second phase of the attack plan. In this phase, an attacker secretly gathers information about their target; the aim is to acquire the relevant data without the victim noticing. The process can be as simple as watching an organization to see when their CEO reports to work or spying on a specific department to see when they down their tools. Because most hackers prefer executing their duties remotely, most passive attacks are conducted over the internet by googling. For example, one may use search engines such as dogpile to search for information about an individual or organization.
- Yahoo or Google search: malicious individuals can use these search engines to gather information about employees of the firm they are targeting to breach their system.
- Surfing online communities like Twitter, Facebook, Instagram can also prove useful sources to gather information about an individual, their lifestyle, and probably a hint to their weakness that can then be exploited.
- The organization’s website may also provide useful information about specific or key individuals within the organization, such as the CEO, MD, head of the IT department, etc. The website can be used to source personal details such as email addresses, phone numbers, roles, etc. With the details, an attacker can then launch a social engineering attack to breach their target.
- Press releases, blogs, newsgroups, and so on, are in some cases, used as the primary channels to gather information about an entity or employees.
- Going through job requirements for a specific position within a company can also help an attacker identify the type of technology being used by a company and the level of competency of their workforce. An attacker can then decide on what method to use when breaching the targeted system from the data.
3. Active Attacks
An active attack involves closely examining the network to discover individual hosts and verify the validity of the gathered information, such as the type of operating system in use, IP address of the given gadget, and available services on the network, collected during the passive attack. It involves the risk of detection and can also be referred to as “Active reconnaissance” or “Rattling the doorknobs”.
Active reconnaissance can be used to confirm the security measures put in place by an attacker, but at the same time, it can alert the victim if not well executed. The process may raise suspicion or increase the attacker’s chance of being caught before they execute the full attack.
4. Scrutinizing and Scanning the Gathered Information
Scanning is a key step to intelligently examine after as you collect information about the network infrastructure. The process has the following objectives;
- Network scanning is executed to understand better the IP address and other related information about the computer network system.
- Port Scanning – to identify any closed or open ports and services
- Vulnerability scanning – to identify existing weak links within the system.
In the hacking world, the scrutinizing phase is also referred to as enumeration. The objective of scrutinizing includes:
- To validate the authenticity of the user running the given account, be it an individual or a group of persons.
- To identify network resources and or shared resources
- To verify the operating system and various applications that are running on the computer OS.
5. Attack
The attack phase is the last step in the attack process. It involves the hacker gaining and maintaining full control of the system access. It comes immediately after scanning and enumeration, and it launched sequentially as listed in the below steps.
- Brute force attack or any other relevant method to bypass the password.
- Exploit the password.
- Launch the malicious command or applications.
- If requires, then hide the files.
- Cover the tracks, don’t leave any trail that can lead back to you as the malicious third party. This can be achieved by deleting logs so that there is no trail for your illicit actions.
The Deep Web
The deep web is the core of online underground cybercrime activities. It is inaccessible with the standard browsers and can also not be indexed by the available search engines. It entails the dark web as the most significant component. Other components include TOR, Invisible Internet Project, and Freenet.
The deep web can only be accessed by very sophisticated technologies as most owners of the site prefer to remain unknown. The contents of these websites are hidden from the general public and can only be accessed by those with A-level computing skills. The Onion Router (Tor) is used to access the Deep Web, as the browsers allow one to surf anonymously and hide your IP address with a different one.
The Deep Web is a paradise for cybercriminals. Underworld criminals can freely trade in illegal drugs, buy and sell malware, crimeware, ransomware, identity cards, deal with cyber-laundering, credit cards, and the list goes on and on.
Conclusion
Cybercrime is a complicated and vast phenomenon. The rapid increase in phones, Wi-Fi networks, and the internet has increased the complexity and cyber-attacks. The advancement in technology has led to an expansion in cyber-criminality and the cyber victimization of the vast ignorant population.
Protection against cybercriminal activities starts with taking individual precautionary measures. It then expands to organizational, corporate, military, societal, national, and international levels. Comprehensive protection at all levels and the installation of various layers of security minimizes, prevents, and decelerates the rate of cybercrime.
Most hackers use the commonly available tools to exploit the less knowledgeable population. Installing the right technology at your organization or personal level alone is not enough to efficiently protect against cybercrime.
Integration of fields such as awareness, employee training, culture, social aspects, laws, International corporations, and prosecutions are needed to blend with technical solutions to tackle cybercrime. Of course, it is essential to understand how cybercriminals plan attacks.
The creation of national governance and International entities formed by various countries to prosecute cybercriminals are areas to be improved. Cybersecurity is a global responsibility and should be jointly handled by major countries across the globe, if not all. Train your employees. Please give them the right technology, and always be woke to avoid the fatal damages caused by cybercriminal activities.