Why Passwords Suck
Usernames and Passwords are not secure by nature. Usernames and Passwords are controls that rely on “Something you know.” Knowledge is easily transferable, and therefore, passwords are not secure.
No amount of security training will eliminate or overcome human nature. It is human nature to make passwords we can easily remember. Passwords that are easy for us to remember are also easy for people to guess. Passwords are also used over and over again on multiple accounts – bank accounts, email accounts, work accounts, etc.
Worse yet, passwords our often openly shared among trusted individuals like family members. That shared Netflix account email and password can, in some cases, also access many other accounts that the user has.
Therefore, Two Factor Authentication became necessary
By combining Passwords with Bio-metrics (Something you are) or a Smart Card (Something you have), the authentication is much more secure.
Requiring a one time password from an RSA token or smartphone soft token along with a password is now the norm for signing into corporate systems. You have to know the password and also have to possess the device to sign-in securely.
Bio-metrics, like the use of a fingerprint reader or retina scan, is less common but also very effective when combined with the need for a password.
The need for two-factor authentication reiterates that passwords suck.
There must be something better. There is.
SQRL (Squirrel) will destroy the need for Logins and Passwords
SQRL stands for “Secure Quick Reliable Login”. SQRL is the brainchild of one of the superstars in cybersecurity, Steve Gibson. Steve Gibson runs the Security Now podcast. He is also the author of many cybersecurity books. Steve is one of my favorite people in the cybersecurity space.
Steve and his team have been developing SQRL since the inception of the idea in 2013. This protocol/method is still under development, but it appears that it is near ready for prime time. You can demo SQRL at Gibson Research.
The cool thing about SQRL is that it is entirely free and open, and it will always be that way. Steve Gibson created SQRL to fill a need and not to make money. Thousands of hours of development and research were “donated” for the good of the cyber world – a very noble thing indeed!
Here is the login page for the SQRL demo:
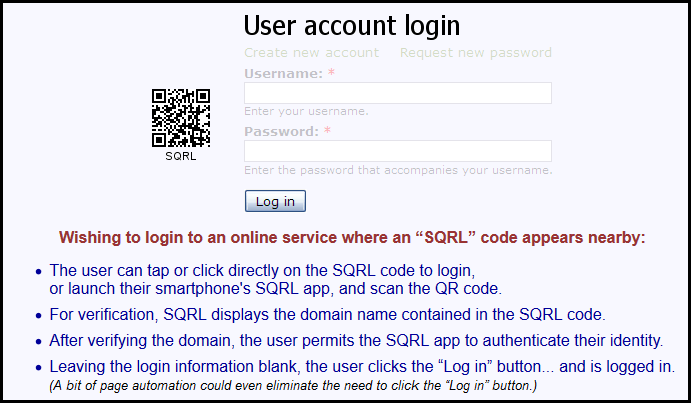
To make this work, you will have an SQRL app on your phone. This app would contain a private key.
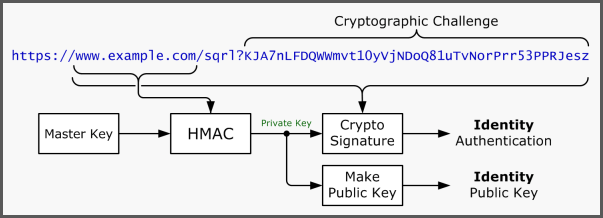
The QR code (like in the above image) contains the URL and the domain of the site that you are trying to connect to. By scanning the QR code, you are creating a public/private key pair by using a hashing function (HMAC) with your master key and the domain name of the site.
Your phone app would then transmit your public key to the site as your identity. The encrypted QR code is transmitted to authenticate you.
Your public key takes the place of your username. The encrypted QR code takes the place of your password.
Your public key is a constant – it does not change. So, the website you are accessing will always know that it is you.
Because the QR code is encrypted with your private key, the website can verify that you possess the matching private key without knowing the private key itself.
The SQRL process is both simple and brilliant.
Steve Gibson’s process drawing shows the steps:
The Amazing Advantages
SQRL is Ridiculously Easy to Use
One of the best things about this system is that it allows you to authenticate at a website very quickly with little effort. The user will not have to create a website account by typing in their email address and creating a password.
After you set up SQRL, when you want to create an account at a blog or any website, it is as simple as clicking on the SQRL emblem. One step is all that you need. It is effortless. People call this “frictionless”.
SQRL is Simple
While SQRL is ingenious, it is also very simple. This simplicity means that there is not a lot that can go wrong. Because it is so simple, it is unlikely that there will need to be bug fixes.
SQRL is Very Secure
You should never see SQRL being the cause of any data losses due to hacking or social engineering. The very nature of SQRL makes it secure. A breach would mean that a hacker would have obtained the public keys of the users.
But nobody really should care if their public key is exposed.
Your public key is, as the name implies, public. The hacker would not be able to impersonate the users because the users’ private key remains private.
SQRL is better than using Facebook or Google to create a log in.
Using Facebook and Google to create logins for websites is very easy but has a much higher security risk. Using this method makes you rely on a third party website for authentication. When the third party website gets compromised, then every login that you have is compromised. This snowball effect is not an ideal situation when it comes to security.
How Will SQRL Unfold?
Right now there are relatively few people who know about SQRL, how it works, and the advantages of it. Only security geeks (like myself), and fans of Steve Gibson (also like myself) have a good knowledge of how SQRL works and the power of it.
I expect that Steve and the team will finish developing SQRL soon. I look forward to the official launch. The rollout will be very slow as only security nerds will initially jump on it. But, when its power becomes fully known, SQRL will begin gaining traction and press.
The folks at TechCrunch will do a story for sure.
Soon, SQRL will take over the web as the security standard for websites. You will be hard-pressed to find a WordPress site that is not using SQRL. If your site is not using SQRL, then you will be at a disadvantage.
I see SQRL as the future. Let’s see if it unfolds the way I see it.