What do virtually all Phishing Emails have in common? By understanding what Phishing Emails have in common, you can quickly identify them and avoid these threats.
What is phishing?
Phishing is a method used by hackers to collect personal information using deceptive e-mails and websites. It’s a form of attack that uses disguised email as a weapon.
The main objective is to trick the target into believing that the message is legitimate. It could be crafted to look like a note from a senior employee within their firm. Sometimes they are made to look like a request from their bank. It may direct the victim to download an attachment or to click to link.
However, phishing emails are distinct and can be easily identified by someone who is well informed about the characteristics of this kind of cyber-attack.
In most cases, phishing emails appear to be from a real person, a trusted entity, or a company with which the target is likely to do business.
Phishing attacks are one of the oldest techniques used in cyberattacks, dating back to the 1990s. Despite being in existence for quite some time, phishing attacks are becoming more sophisticated and sinister with a rapid technological development rate.
Phishing is still one of the most widespread and most exploited techniques by black-hats, especially during crises such as SARS or COVID-19.
In this article, we will address some of the striking similarities between various phishing emails. We will look at multiple types of phishing attacks. We will describe vulnerabilities mostly exploited and show how to position your company or yourself against such security incidences.
Phishing Kit
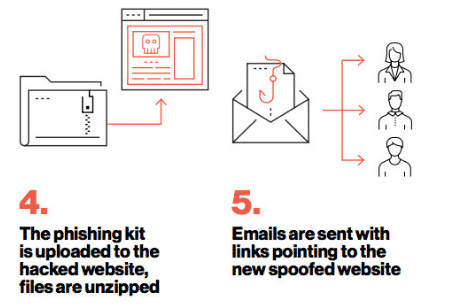
A phishing kit is a collection of software tools that makes it easier for people with little or no technical skills to execute an attack. A typical phishing kit is made of website development software with a simple, low/no-code graphical user interface (GUI).
The phishing kit comes complete with graphics, sample scripts, and email templates that an attacker can readily use to create legitimate correspondences. Some phishing kits come along with telephone numbers, a list of vulnerable e-mail addresses, and various software to automate the malware distribution process. 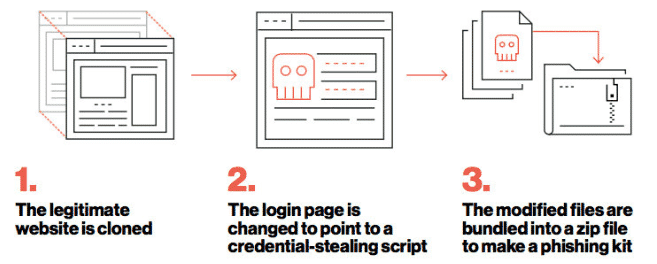
Types of phishing
One thing that all phishing emails have in common is the disguise. Attackers cover their email address so that it looks like it’s coming from a legitimate user. Or, they create fake websites that look like legitimate ones trusted by the target. In some cases, they use foreign character sets to disguise URLs.
With that in mind, we can classify various forms of attack as phishing attacks. Classification can be done in several ways, including the purpose of the phishing attempt, intrusion technique, etc. Generally, phishing emails aims at two things:
- Trick the victim into handing over sensitive information, often a username and a password, that the attacker can easily breach a system or account.
- Download malware. In this case, an attacker aims at deceiving the target to infect their computer by installing malware or a local access Trojan to infect their computers. For instance, a phishing mail may be sent to an HR officer with an attachment that claims to be a job seekers’ resume. The attachments are mostly in .zip files or Microsoft Office documents embedded with malicious codes or links.
1. Email Phishing
Most phishing attacks are sent via email. In these techniques, the hacker sets up a fake domain that mimics a genuine organization and then sends lots of generic requests to an identified target through the mail. The fraudulent substitution always involves replacing characters, such as ‘n’ and ‘r’ (‘rn’)close to each other to appear as ‘m’. In some cases, the crooks may decide to use the organization’s name in the domain, such as [email protected], hoping that it will appear as ALIBABA in the target’s inbox.
There are several ways to spot a phishing email, and by the end of this article, you should be able to spot one quickly. You will also be able to guide others to identify Phishing emails.
As a general rule, always check and carefully scrutinize the email address of a message asking you to click a link or download an attachment. It is also wise to run an email lookup on unknown emails so that you can stay safe from potential phishing scams.
2. Whaling
Whaling attacks target senior executives. Despite having the same goal as any other form of a phishing attack, whaling attacks tend to be more subtle.
Because the technique is used on high-profile individuals within an organization, the methodology does not employ fake links and malicious URLs in breaching a system.
There have been increasing cases of whaling attacks on various sectors involving bogus tax returns in the recent past. Tax forms are valuable to hackers. They contain a wealth of important information such as social security numbers, addresses, bank account information, and the targeted individual’s official full names.
3. Vishing and Smishing
When using either vishing or smishing techniques to hack a target, telephones replace emails as the primary communication method.
In smishing attacks, a cybercriminal sends phishing texts to a target through text messages using a telephone. The message is drafted and tuned just as the email could have been. The objective is to convince the victim that the message is from a legitimate or trusted source.
In Vishing attacks, the cyber-criminal deceives its target through an actual phone call.
One of the common tricks used by hackers to execute a vishing attack is posing as a fraud investigator. The attacker may pose to be from a card company or a bank and pretend to inform the target about accounts that were breached.
4. Spear Phishing
Spear phishing is a sophisticated method of attack involving email. This technique is used to breach a specific person. Cyber-criminals who exploit their targets through these techniques already have some information about their targets, such as;
- Name and physical address
- Place of employments
- Title of job
- Specific information about duty at work
- Email address
One of the most detrimental phishing attacks ever done, the hacking of the Democratic National Committee, was accomplished with the aid of spear phishing. The first round of attacks involved sending emails containing malicious attacks to more than 1 000 email addresses. The second wave of the attack led to a better part of the committee members sharing their passwords.
5. Angler Phishing
Social media platforms have given hackers a new attack vector. There are various fake URLs, tweets, cloned websites, instant messaging techniques, and posts that can be used to persuade people to download malware or divulge sensitive information.
For instance, Elon Musk and Bill Gates are among the top profiles whose Twitter accounts have been recently used to spike attacks. The latest one was done using bitcoins and a message convincing targets to give back to society.
Data willingly posted by people can also be used to create highly targeted attacks. In 2016, a group of hackers conducted a sophisticated attack through Facebook. Facebook users received messages informing them that they had been mentioned in a post. Cyber-criminals initiated this message. Upon clicking the link, it would install malware or Trojan into their personal computers. The second phase of the attack comprised of the target’s account being breached. Immediately, they used the compromised web browser to access their Facebook account. The hackers managed to control various accounts, steal important data, and spread the infection to victims’ friends through their accounts.
What do Virtually all Phishing Emails have in Common?
1. The message is sent from a public email domain
There’s no legitimate organization that can send emails from an address that ends with ‘@gmail.com’. Not even Google can use such addresses. Most organizations, even the small ones, have their domain and company accounts. For instance, Google is most likely to use ‘@google.com’ when sending legitimate emails to their clients. Therefore, if the domain names match that of the sender, the message is probably from a legitimate user, and the message is most likely to be legitimate.
You can always verify an organization’s domain name by typing the company’s name into a reliable search engine. This makes it simple to detect phishing emails. However, cybercriminals are more advanced, and therefore it requires one to be more vigilant to detect these intruders.
An important tip to note: look at the email address and not just the sender.
Below is a phishing mail mimicking PayPal. Most crooks can create bogus email addresses and even select a display name that does not relate to the email in any way.
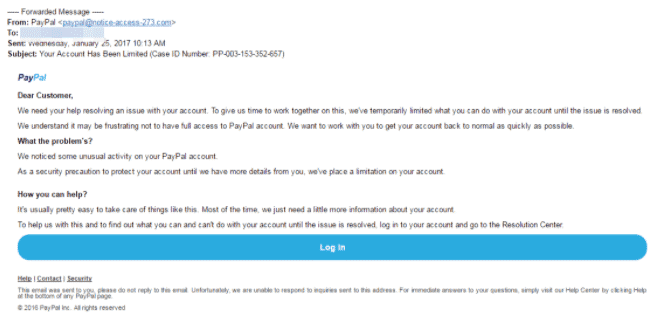
This is a nearly flawless scam email. It is professionally styled and believable. The email uses PayPal’s logo at the top of the message, making it undetectable to an ‘ignorant’ target. However, there’s a huge red flag; the sender’s address is noted as ‘[email protected]’ instead of having an organization name in the domain to indicate that it had come from an individual at PayPal, for instance, (@) PayPal.
Most hackers maximize their target ignorance, and in most cases, mere inclusions of a known company name anywhere in the message are enough to trick people. The targeted individual may glance at the word PayPal in the email address and be satisfied. In some cases, others may not even differentiate between the domain name and the local part of the address.
2. They are poorly written emails with an odd writing tone
Poor spelling and grammar should always be the first red flag for any email received, whether from a known or unknown source. Some people are convinced that such errors arise due to an inefficient “filtering system”; however, hackers exploit this technique on the most gullible targets only. The catch here is that if an individual is unable to pick the minor hints at the first stages of the intrusion, then most likely, they won’t be able to pick clues during the scammer’s endgame.
Automated attacks
When executing a phishing attack, hackers do not have to monitor inboxes and send tailored responses. To reach a wider audience and lure more victims, they prefer randomly dumping thousands of crafted messages on unsuspecting persons.
Important tip: look for grammatical errors and not spelling mistakes.
In most cases, hackers will use a translation machine or spellchecker when crafting phishing messages. These apps can give the right words with accuracies close to 100, but they do not necessarily arrange the words into the proper context.
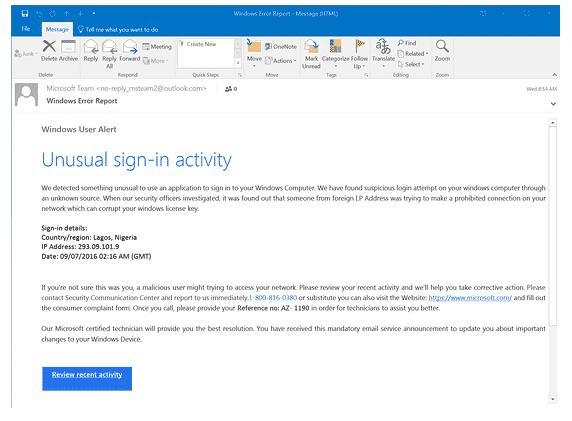
For example, the image shown above is a phishing scam imitating windows. Every word is spelled correctly except for various minor grammatical errors that a native English speaker wouldn’t make, such as “We detected something unusual to use an application.” There is also an array of missed words in various sentences such as “Please contact Security Communication Center,” “a malicious user might trying to access,” etc.
Everyone makes typing mistakes from time to time and especially when in a hurry; however, you should be able to thoroughly scrutinize the error if it’s a clue to something more sinister.
3. There are suspicious attachments or links
Phishing emails are launched in various forms. Although this article has majorly focused on email phishing, scammers can also use phone calls, social media posts, and text messages.
However, despite the channel or techniques through which phishing emails are presented, they will always contain a payload. All phishing emails are embedded with links to bogus websites or infected attachments, prompting you to download them.
An infected attachment, in this case, is any document that contains malware. Below is an ideal example of a phisher claiming to send an invoice.
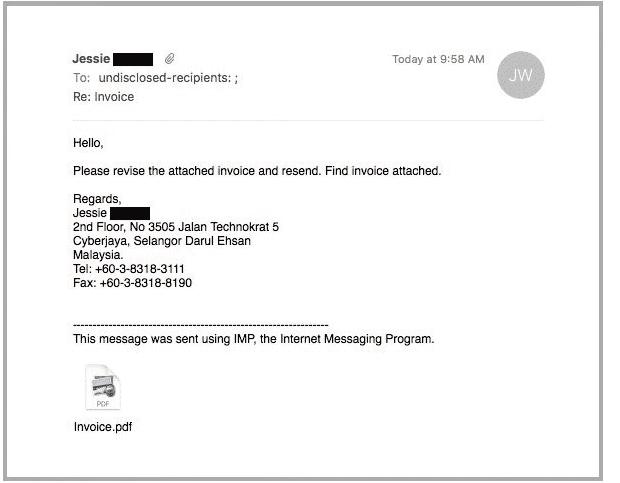
From the above image, it’s impossible to know what the message entails until they open the attachment, whether the recipient was expecting to receive an invoice from the sender or not. Upon opening the message, the receiver will realize that the message is not intended for them, but then it will be too late, and the malware will have been unleashed on their computers.
4. There’s a sense of urgency, or the message calls for prompt action.
Hackers are aware that most human beings are procrastinators. Despite the significance of the message, most people will decide to deal with the information later.
The law of nature has it that the more you think or focus on something, the more likely you notice that something is off. Maybe in the day, you realize that the claimed organization doesn’t contact you at the same address, or perhaps you realize that your other colleagues at work did not receive the same email. Even if you don’t get the “Ahaa!” moment, reading the message with fresh eyes might unveil its true nature.
And for these reasons, most phishing emails request that you act immediately or that chance will be gone. A trait that is very evident in almost every example we’ve used above.
Below is a typical example:
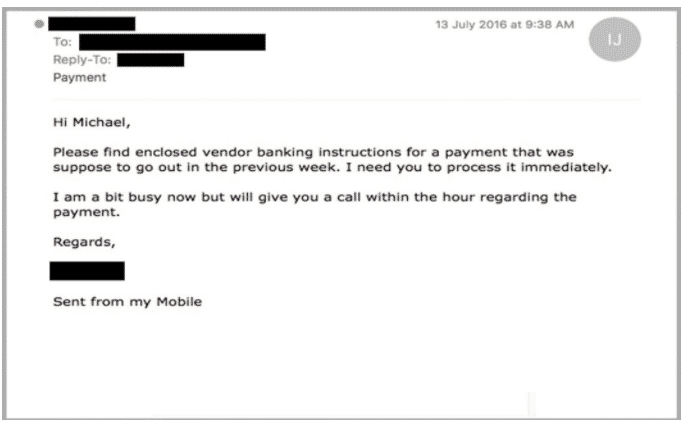
Such phishing scams are very sinister and dangerous at the same time since it jeopardizes the recipients’ (possibly a junior employee) position at work.
5. They have Oddly Generic Greetings
Phishing scammers target millions of people and therefore send lots of phishing emails a day. With this work volume, they heavily rely on phishing tools or applications to help them generate phishing templates. Commonly used greetings include “Dear Customer” implying “Your Company” or “Your Bank.” This kind of sensitive email should have more details about you as they originate from someone who knows you better, a partner you’ve met before, or a colleague you once served with at the same workstation.
Educate your employees to prevent phishing
Education is power, and knowledge liberates. Regularly remind your employees of what they should be looking for when handling mails or information within the organization. This does not necessarily mean having frequent awareness training programs as a few well-placed posters within the office can serve the purpose.