Biometrics is an element ingredient of cybersecurity. Technology makes things more comfortable, but rapid advancements come with new flaws and challenges. This makes security a primary concern. Protection of cyber-space from identity theft, theft of data, or even computer resources is referred to as cybersecurity. Hackers are continually evolving. As technology advances, they also take advantage of the new tools and skills and set security systems, making passwords inefficient as a protective mechanism.
Because of such reasons, biometric security is fast gaining widespread adoption among companies, organizations, and individuals as the preferred way to safeguard cyber-space from hackers and other malicious individuals. Led by tech giants such as Apple Inc., technologies such as facial recognition, fingerprint scanners, and iris scans have become mainstream.
Technology plays a significant role in fighting cybercrime, although it has associated risks as well. The two primary issues that organizations and individuals need to be aware of to enjoy the full benefits of biometric security and protect the digital information they hold can be stated as:
- Organizations and individuals need to understand that they are not immune to attacks. Facial recognition and fingerprint can still be penetrated by cybercriminals to either spoof or steal biometric data.
- Organizations holding extremely significant third-party data such as financial institutions and hospitals should understand the security implications of a data breach and their potential liability in case of an incidence.
For sensitive documents, advanced biometrics are used to provide an extra layer of protection. For instance, voice recognition is already being used by Citibank to identify clients. The British bank Halifax is also developing devices to monitor heartbeat as a mechanism to verify their customer’s identities.
In the automobile industry, Ford is incorporating biometric sensors in their cars to enhance security. The technology does not only perform a one check on the driver. Instead, it analyzes users’ behavior in real-time to verify whether or not they are themselves throughout the entire session that they are logged on to the digital platform.
Is Biometrics Cybersecurity indicating a New Age in Cybersecurity?
Yes, it appears so. And there is no doubt that the technology would bring massive improvements to cybersecurity infrastructure. The techniques make it more difficult for hackers to access systems remotely. Even with the passwords at hand, hackers still need various biometric scans to penetrate a network. The technology has been designed and developed to be a one-stop system. But can it stand alone in providing ultimate protection to data? Let’s have a look.
Is Biometrics cybersecurity sufficient on its own?
You know that ace hackers easily fool these systems for anyone who has ever watched a spy movie. If you protect your systems with facial recognition as the biometric protection of choice, then theoretically, a highly skilled hacker would still manage to penetrate using a high-quality photo of you facing the camera.
The point here is, if someone is desperate to hack your system, then they will do everything possible. So, as much as biometric security is a step in the right direction, it should be an extra layer of protection and not a stand-alone technique.
Functionalities of a Biometric System
Biometrics is not only a fascinating invention to learn and read about. It can be a highly enabling technology if it is carefully used. The technology can be used to reduce cybercrime, provide user-friendly machines, and provide a safer society through the following three basic functionalities;
1.Verification – is this really Legit Joe? Based on the biometric data stored in the servers, the technology can, with high certainty verifies a claimed enrollment authentication. For example, suppose a person claims that they are Legit Joe within the authentication system and gives their fingerprint. The system compares the offered fingerprint to the one enrolled in the system and is associated with the claimed identity. If the two matches, then the person is granted access. The person is denied entry if they differ. 2.Identification – this is merely determining whether the person is in or not in the database. There may be millions of enrolled identities in the database. The system counterchecks the given biometric data and what is stored to identify if there is any correlation. Some of the typical identification applications include criminal investigation, parenthood determination, welfare disbursement, voter identification cards, identification of missing children, border control, etc. 3.Screening – to determine whether an individual is on the watchlist radar. For instance, the screening services can be used as security in public rallies, airport security, and other surveillance activities.
Different types of Approaches to Biometrics
Biometric technologies use an array of physical characteristics, with some being more secure than others. We’ll now look into some of these solutions that focus on recognizing the following physical traits;
- Iris pattern
- Voice
- Fingerprints
- Vein patterns
- Typing behavior
- Facial structure
The list consists of just a sample of physical characteristics used better to understand the technology and not all the features. For instance, you can notice that retinal scans have not been included. However, as we examine some of the setbacks facing the listed technologies, you can use the same ideology as missing from the list.
So how does the technology work?
Biometric security is a sequential process executed in a specific order; it starts with enrollment, then storage of the enrollment to management, scanning, verification of the offered data, and finally to object integration. Below is an outline of the steps;
Step 1: the first stage is the enrollment stage, where an administrator supervises the collection of one or more biological characteristics. This is done through a sensor that is connected to the biometrics enrollment application.
Step 2: the enrollment application creates a reference template.
Step 3: the template is then connected to a user’s identification and stored in a database.
Below is a diagram representation of the biometric model.
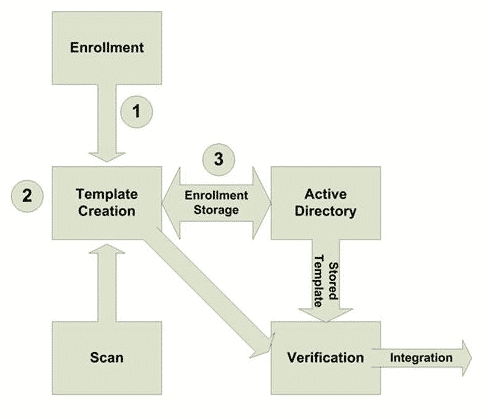
In the case of an employee working for a given organization, they will be required to provide the specific characteristics collected during enrollment for them to begin work.
Evaluating Biometrics
There are various types of biometrics, and they differ in multiple ways. A unique set of advantages and disadvantages is associated with every approach that necessitates careful analysis while selecting a solution for specific access control. Therefore, before we examine the above-listed biometrics technologies, let us look at some of the setbacks experienced while implementing these solutions, such as;
• Enrollment risks • Business continuity • Forgery • Datastore contamination • Accuracy
Enrollment risks
The enrollment process is delicate, and there are possibilities of human error or error due to inadequate vendor solutions. Remember, the acquired characteristics are stored in a database as a reference template. Therefore, if the reference template is faulty, even to the slightest degree, the same error is reflected at the login time, hence wastage of time and, at worst, denial of access for the right identity. This shows how vulnerable information is at the time of input and how a slight error can lead to a system failure.
Business continuity
Imagine if an enterprise is running on a single Active Directory domain controller. This implies that no one can authenticate if the domain controller fails, and consequently, the business activities will have to terminate.
Forgery
There are body parts that can be easily forged compared to other parts. For example, it’s relatively easy to get a fingerprint impression that seamlessly works for various fingerprint recognition systems compared to generating vein scans.
Datastore contamination
After the reference templates have been stored in the database, the context in which they operate, how the software accesses them, and other attack surface considerations determine the degree of risk of cybercriminals contaminating or replacing the store templates. Suppose the reference templates fall into malicious hands. In that case, they can be used to compromise the systems in various ways, such as using the templates to gain access to the system or creating multiple forgeries of the measured characteristics.
Accuracy
Accuracy challenges are mostly associated with engineering faults during the manufacture of the relevant sensors. Errors in sensors are measured in two ways: false rejection rate and false acceptance rate. If a legitimately enrolled user is scanned and the biometrics system fails, it is a false rejection error. While on the other hand, if a biometric system verifies a person who has not gone through the enrollment process, it is a false acceptance error.
Selecting the right Approach to Biometric Solution
As for the remaining part of the article, we will look at various biometric technologies. Both the pros and cons of every solution as no specific technology can suit all access control challenges.
Fingerprint Recognition
When most people hear of biometrics, all that comes to their mind first is a finger scan. For example, I present one of my index fingers to a fingerprint sensor and key in my phone number to access my school library. Several organizations track their employees’ working hours using fingerprint scanners to monitor clock in and clock out time. Although it is ubiquitous, it has some flaws and can be bypassed by ace hackers; hence not always the right choice.
How does it work?
When you scan your finger, the sensor picks specific characteristics like the one shown in the figure below. The scanned information is then converted to the information referred to as the trial template using an algorithm.
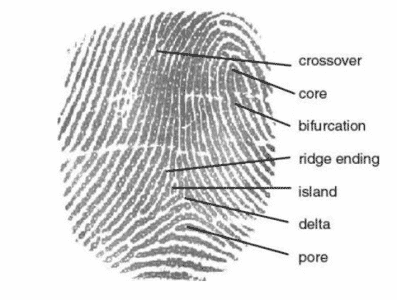
Advantages
- several solutions available
- Less expensive to install compared to other biometric technologies
Disadvantages
- It is highly sensitive to environmental factors
- Ease to forge
Facial Recognition
The technology uses an image of a user’s face to enforce security.
How it works
The technology uses an algorithm to recognize a face in the camera image uniquely. There are databases with different face shapes that help differentiate the human face from other body parts in the camera’s view.
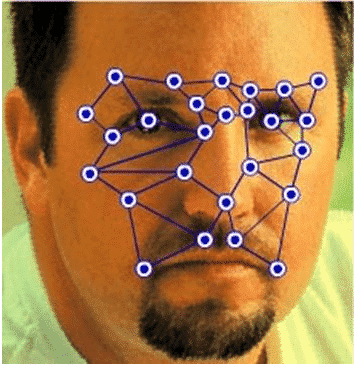
The various nodal points used to identify a user’s face uniquely include
- The shape of the cheekbones
- Jawline length
- Nose width
- Depth of eye sockets.
Advantages
- Difficult to forge
- More acceptable approach compared to contact-based techniques.
- Relatively cheap compared to solutions requiring a separate sensor
- Fast
Disadvantages
- Highly influenced by the lighting of the environment.
- High possibilities of error due to racial differences
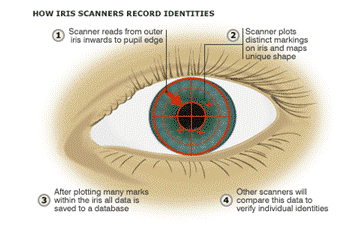
Iris Recognition
Iris scanning is the best solution for looking for high levels of accuracy and low rates of forgery.
How it works
The technology reads retina patterns by shining light into the back of the eye. The data collected is then converted into a reference template for verification, just like other biometric solutions. Below is an image of the human eye (a) and another image showing the iris scanning process (b).
a.
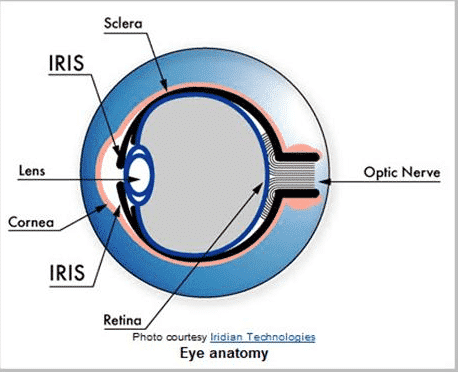
b.
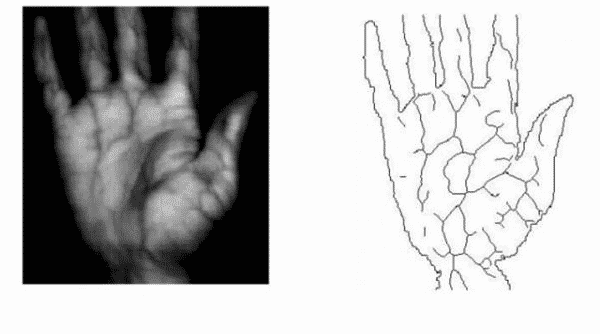
Vein Recognition
There is a complex network of veins lying below our hands. Each individual has a unique pattern that can be used for digital identification. The pattern can be captured using infrared waves and then stored as reference templates for biometric access control. An example of a vein scanner is shown below.

The technology was first engineered by Fujitsu and was designed to be a contactless recognition technology. It relies on specific characteristics of blood in veins known as deoxidized hemoglobin. The blood carried back to the lungs lacks oxygen as the body cells have already consumed that from it. Deoxidized hemoglobin appears black when exposed to light waves of near-infrared wavelength. The ability of deoxidized to absorb such waves and change color makes it easy to identify the unique vein patterns that can then be captured, stored as a reference template, and finally as biometric access control. The picture below illustrates how near-infrared waves extract blood vein patterns.
Advantages
- Likewise to iris recognition, a vein scan does not require physical contact with the sensor.
- The very low error rate
- Nearly impossible to forge
Disadvantages
- This is a new technology that is still evolving, implying that it has no objective standard.
Voice and Typing
Unlike the above-mentioned biometric technologies used to enhance cybersecurity, voice recognition and keystroke dynamics are much less popular and have not gained widespread use.
Voice recognition
Voice recognition is easy to adopt for users, but cybercriminals can easily forge it. The technology uses algorithms to make reference templates using voiceprints. It is less accurate compared to other approaches and subjects to identity theft through recording devices. Voice recognition works well for mobile-based authentication, although it has various hiccups when a user has to speak into a microphone. Thus, voice authentication is highly affected by environmental factors such as background noise, hence not suitable in cubicle-dense areas.
Keystroke dynamics
How slow or fast individual types can be used to identify a person uniquely. The technology is easy to implement in a business setup, though not very accurate. The approach does not require any external gadget, and enrollment automatically occurs as the user executes their day-to-day activities using a computer. When looking for a biometric process that is less expensive, a second layer to multi-factor authentication, and easy to implement, then keystroke dynamic is the technique to go for.
Final thoughts
Technology is fast evolving, creating more attack vectors and increasing attack surfaces. New defense mechanisms come with improvements and security for newly designed threats. However, cybercriminals exploit the latest technologies by using more sophisticated techniques such as deep learning to mimic the voice to overcome approaches such as voice recognition.
Biometrics alone cannot be used as a stand-alone mechanism to protect cyberspace devices because a determined hacker will still find their way through the system. Therefore, biometric security technology should be used as part of a multi-factor authentication system.