Kill Chain cybersecurity is a model that helps in the understanding, identification, and combating of cyber threats. Kill Chain, in its very essence, is a systematic framework to identify stages of cyber attacks. Originated from a military model, Kill Chain now serves as the basis for numerous cybersecurity strategies due to its application in various real-world scenarios, reflecting its significance in today’s digital landscape. A deep dive into this model is not just essential for IT professionals, but for the general public as well to understand how cyber threats can be successfully thwarted.
Understanding Kill Chain Framework
An in-depth look at the Kill Chain cybersecurity framework—its raw functionality, practical implementation, and potential boundary-breaking significance in a rapidly evolving digital landscape.
The digital age ushers in a new epoch, not only of innovation and connectivity but also of uncharted risks and vulnerabilities. Here, in this sphere teeming with technological potential and peril, the Kill Chain cybersecurity framework comes into play as a silver-bullet solution offering strategic insights, situational awareness, and proactive protection against digital threats.
Born in the military domain, Kill Chain was initially a term used to describe a systematic process employed by the military to identify, engage, and neutralize targets. With the advent of cyber-warfare, this method has been adapted into the cybersecurity realm, providing a coherent blueprint to identify, understand, and mitigate cyber threats.
The Kill Chain model, as conceived and developed by Lockheed Martin, operates as an 8-phase process:
- Reconnaissance
- Weaponization
- Delivery
- Exploitation
- Installation
- Command & Control
- Actions on Objectives
- Lateral Movement
The power within this framework lies in its logical and sequential approach to counter-attacks, beginning with the adversary’s initial target scanning (reconnaissance), developing through the generation and delivery of malicious code, evolving into control exertion over the target system, and culminating in the ultimate action phase.
By employing this model, cybersecurity professionals can dissect attacks, identify potential gaps in defense, and strategically position their countermeasures at any stage in the chain. In essence, it provides a panoramic, step-by-step breakdown of an adversary’s attack strategy.
Yet, the scope and impact of the Kill Chain model extend beyond the confines of proactive countermeasures. Through this approach, businesses can curb potential losses by recognizing an attack in its earliest stages. If a potential exploit is identified and neutralized at the first or second stage, a company saves the invaluable resource of time and prevents damaging effects on its infrastructure, reputation, and customer trust.
In this threat-riddled digital age, the Kill Chain framework offers relevance and utility of a twofold nature: cyber defense strategy enhancement and operational cost reduction. While the former is concerned with the systematic dismantling of an adversary’s attack strategy, the latter focuses on minimizing the aftermath of a successful breach, thereby emphasizing the immense preparatory value this step-by-step methodology brings to each organization’s table.
With the constant evolution of cyber threats, the importance of understanding, implementing, and refining a cybersecurity model like the Kill Chain cannot be understated. The digital future calls for an ingenious blend of awareness and adaptability in cybersecurity mechanisms, making the Kill Chain framework a cornerstone in our bold pursuit against cyber adversaries. The value proposition is significant, and the stakes even higher in this ceaseless, virtual battlefield. No doubt, the Kill Chain definitely merits, both for technological enthusiasts and professionals alike, a deeper exploratory dive into its far-reaching implications.
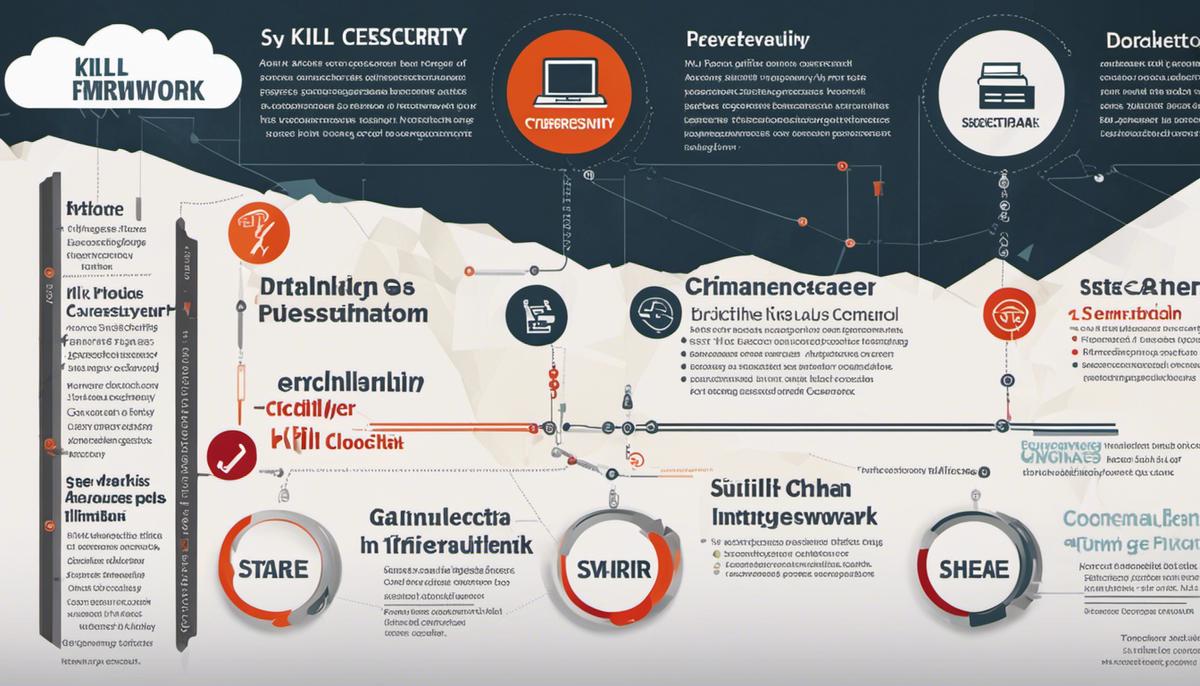
Phases of the Cyber Kill Chain
Deep Dive into the Phases of the Cyber Kill Chain
Moving beyond the general understanding of the Kill Chain model, it’s essential to take a hard look at each phase. This framework takes cybersecurity beyond countering random threats and pushes it toward understanding a cyber-attacker’s step-by-step game plan. An in-depth look reveals just how crucial each stage is in creating a resilient cyber defense strategy.
The reconnaissance phase is the first step, a period of gathering cyber intelligence about potential attack targets. It’s the online equivalent of carefully studying blueprints to strategize the perfect heist. Information extracted during this phase ranges from system vulnerabilities to personal data, providing a fertile foundation for a pending targeted attack.
The weaponization stage follows, where collected information is fashioned into an effective cyber weapon. Attackers design malware or exploit known vulnerabilities to serve their malicious objectives. This specific phase, invisible to the target, poses significant detection challenges.
The delivery phase sets things into motion. The proverbial horse trojan, laden with its deadly payload, gears up for its surreptitious journey. It could be an innocent-enough-looking email attachment, web download, or USB device. Technology has enabled multiple delivery channels making this phase increasingly unpredictable.
The exploitation stage is where potential vulnerabilities are exploited, and the attack comes to life. The simple click of a deceitful link opens the gateway for an attacker’s initial foothold into the system.
We then move into the installation phase. Here, the planted malware begins to secure its position within the compromised system. It may seek out additional privileges, establish a presence to withstand restarts, and initiate its planned operation.
The command-and-control (C2) stage is a critical junction where malware starts communicating with the attacker’s server. This connectivity provides an attacker with remote control and command over the infected system. An effective C2 communication can make it seem like business as usual even as confidential data slips away unobtrusively.
Finally, the actions-on-objectives phase seals the cyberattack by achieving its predefined aims. These could vary from data theft, system disruption, distributing ransomware, or even preparing for a more complex, longer-term invasive operation.
To thwart such a multifaceted attack process requires a robust cyber defense strategy that disrupts this kill chain at multiple points. Proactive monitoring, intrusion detection systems, and regular system audits form solid lines of defense.
More importantly, it’s crucial to stay one step ahead, for cybersecurity is not a static battleground but an arena of constant evolution. Understanding the cyber kill chain leverages knowledge into the superior firepower needed for this tireless war against invisible adversaries. Remember, in the digital realm, an ounce of prevention can indeed defer a considerable breach.
Kill Chain vs. Attack lifecycle.
Understanding what sets the Cyber Kill Chain apart from the basic attack life cycle is crucial in developing an effective cybersecurity defense. This demarcation largely lies in the enhanced depth, focus, and systematic approach that the Kill Chain model adheres to.
While the standard attack life cycle is typically vague, describing the stages that a cyber assault might take, the Cyber Kill Chain model takes it a notch higher. It breaks down the stages into a much more nuanced and comprehensive process.
Let’s delve in, shall we?
Critically, the Cyber Kill Chain is built upon the notion that each attack is not a singular action but a series of linked stages, each requiring successful execution for the next phase to be initiated. This interconnected view gives security professionals the opportunity to interrupt an attack at various points before it reaches its end objective.
Moreover, the Kill Chain model puts considerable attention on adversary behavior and tactics. It emphasizes understanding the attacker’s mindset and modus operandi rather than focusing solely on the technical aspects of the attack. This approach provides defenders with a deeper insight into cyber threats and assists in the development of strategies that directly counter enemy movements.
One noteworthy aspect that sets the Cyber Kill Chain apart from others is its dynamic nature. Because it emphasizes understanding an attacker’s behavior, it becomes inherently equipped to evolve with the changing tactics, techniques, and procedures of attackers. This is in contrast to static defense mechanisms, which usually struggle to cope with new and emerging threats.
Further, the Cyber Kill Chain model acts as guide for cyber threat intelligence. It enables organizations to map out adversary’s planned actions, predict future steps, and proactively defend their networks. On the contrary, the generic attack lifecycle generally lacks this feature of predictive capability.
Another significant differentiator is the Kill Chain’s ability to detect Cyber threats early in the progression of the attack. Early detection is crucial as it allows potential targets to disrupt the progression of the attack before serious damage is done. The traditional attack life cycle does not afford such a tactical advantage.
Finally, the Cyber Kill Chain model is much more granular in its approach, providing a step-by-step framework that is designed to be easy to understand and implement. On the other hand, the generic attack life cycle lacks this distinct structuring and clarity.
In the high-stakes world of cyber warfare, understanding the tactics and strategy of your opponent is the key to a strong defense. The Cyber Kill Chain model gives you a strategic advantage, allowing you to anticipate, detect, and counter-attacks. Equipped with this model, tech enthusiasts can be well on their way to bolstering their cyber defense arsenal. Automation, understanding, and a dogged determination to fend off attacks never seemed so thrilling!
Implementation of Kill Chain
Given that a complete understanding of the Cyberspace Kill Chain model has been provided, it’s time to explore the real-world application of this framework. The implementation of the Kill Chain model should be a well-thought and meticulously planned method. The cornerstone of practical implementation is the skilled security teams capable of integrating this model into the existing system.
Security teams should be proficient in discerning the various phases of the Kill Chain model and mapping them to threat indicators in their specific environments. They should be capable of recognizing potential vulnerabilities that may present opportunities at different stages of the Kill Chain. A proactive approach to anticipating cyber threats and early preventative action is vital to implement this model effectively.
In the defense context, the integration of intrusion detection systems (IDS) and security information and event management systems (SIEM) is the first step to emulating the Kill Chain methodology in real-world scenarios. IDS aligned with the Kill Chain model can detect the early stages of an attack, such as reconnaissance and weaponization. SIEM, on the other hand, provides the necessary analytical insights needed in later stages, like delivery and exploitation by correlating numerous events and forming a holistic view.
Automated workflows are also a crucial part of the Kill Chain implementation. Automation can be utilized to react to specific IDS alerts and SIEM events; it can block or deflect known malicious traffic, enforce stricter security policies, or issue alerts for manual review. This not only eliminates the need for manual intervention at every stage but also expedites the response time, leading to effective damage control.
Segmentation is another practice that aligns with the Kill Chain model’s philosophy. By dividing the network into various segments, one ensures the limitation of the attacker only to that particular zone. This mitigates the risk of the attacker navigating through the network and reduces the potential impact of a breach.
A crucial part of practically implementing the Kill Chain model is continuous learning. Organizations need to be in sync with the ever-evolving threat landscape and must review and modify their security posture in tandem. Keeping abreast with the latest in cyber threat intelligence, sharing information with other organizations, and applying learned insights provide an element of constant evolution vital to the effective use of the Kill Chain model.
In a nutshell, the Kill Chain model can be seamlessly integrated into an organization’s security protocol by vigilant mapping of the Kill Chain stages to threat indicators, proactive anticipation of cyber threats, systemizing automation and segmentation, and a commitment to continuous learning. Leveraging the Kill Chain model can move an organization’s cybersecurity defense from reactive to proactive, with a strong capability to predict, deter, and counter the prevailing cyber threats in our digital era.

Future of Kill Chain Cybersecurity
Advancing The Kill Chain Model – A New Chapter In Cybersecurity
Despite our comprehensive dive into understanding the Cyber Kill Chain model, its crucial role in strengthening cybersecurity defense and its dynamic adaptability to morphing cyber threats, we understand its relevance is more critical than ever. Let’s explore the next frontier – how the Kill Chain model is evolving and what insights we have into the future of this cybersecurity framework.
Notably, evolving hacker techniques are compelling a transformation in the Kill Chain model. It’s no revelation that cyber adversaries are agile, always probing for novel ways to breach security. This complexity necessitates a transition from a primarily linear progression in the model, making way for multiple parallel chains running concurrently. The threat landscape is multinational now – a single cyber attack can have diverse origins, methodologies, and purposes.
Machine learning (ML) and artificial intelligence (AI) are destined to take the Kill Chain to the next level. Automated tracking and neutralizing attacks at machine speed are the aspirations. With the vast capacity of ML and AI to analyze data, augmenting the Kill Chain with AI capabilities will vastly improve early detection. Visualizing the modern threat landscape thus becomes less daunting through the lens of predictive analytics.
Likewise, integrating cloud technology is another stride forward for the Kill Chain model. As organizations adopt cloud services, they must adapt their cybersecurity measures, too. Cloud-enabled Kill Chain models provide a more seamless view of potential threats across all touchpoints – network, applications, data, endpoints, and users.
Moreover, the human element shouldn’t be overlooked. An evolving Kill Chain model considers robust user awareness and training, ensuring human interactions with systems are guided by an informed, security-conscious mindset. Ultimately, it reminds us that technology can provide the tools, but it’s still human choices that can help prevent making the cyberthreat landscape even more fertile.
Consider also the growth of Decentralized Cybersecurity models that incorporate Kill Chain principles. Even as enterprises continue to centralize threat intelligence and response orchestrations, there’s a growing realization that individual nodes (devices or software applications) should have their unique security cover. The premise is simple – empowering each node with actionable threat intelligence, leveraging AI/ML, and tailored responses.
Observe, too, the shift from a threat-focused Kill Chain model to a more preventive, resilience-focused model. Building cyber resilience is about more than just detecting and deflecting attacks but preparing for inevitable successful breaches. In an era where it’s not about ‘if’ but ‘when’ an attack occurs, rapid response and recovery are as essential as prevention.
All in all, the future looks bright (and complex) for the Kill Chain model. There’s boundless potential for an evolved model aided by AI, machine learning, and cloud computing, as well as a more involved human element and decentralization. This continuing transformation is inexorable, driven by an equally ever-changing array of cyber threats. The name of the cybersecurity game isn’t static defense but dynamic – and strategic – evolution.
As we look to the future of Kill Chain in cybersecurity, it becomes clear that it will continue to evolve based on emerging trends and advancements in technology. Its implementation within an organizational framework, though not without its challenges, remains vital to ensure robust data security. The comparison with standard attack lifecycles aids in distinguishing its unique strengths and appropriate application. Cyberthreats, after all, are relentlessly becoming more sophisticated. Thus, a deep comprehension of the Kill Chain framework, its phases, and its probable improvements speaks not only to the understanding of cyber attacks’ anatomy but also to proactively fortifying our defenses in an increasingly interconnected world.

