.
Cyber attacks are a threat to businesses of all sizes and in all industries. With cybercrime rising by 600% during the pandemic, businesses are more vulnerable than ever to the financial and reputational repercussions of cyberattacks.
To help business owners prevent and respond to such incidents, this guide will go over statistics on types of cyberattacks and actionable tips to prevent them.
Costs of Cybercrime
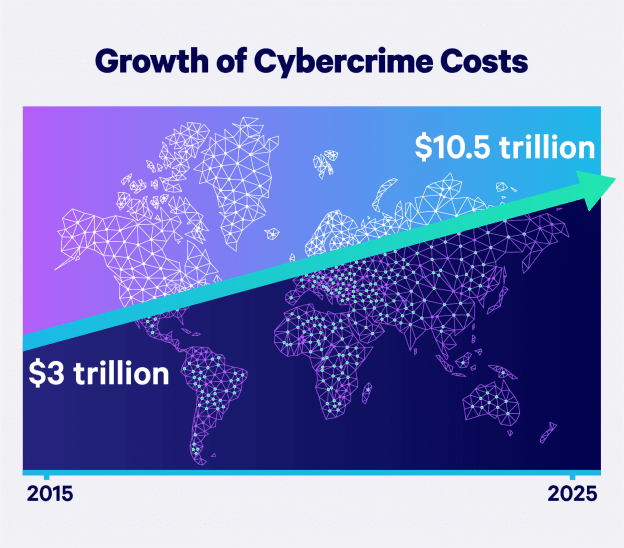
By 2025, it is estimated that cybercrime will cost businesses worldwide $10.5 trillion annually. With the global cost of cybercrime at $3 trillion in 2015, that’s more than a threefold increase over a decade.
.
.
Small businesses are particularly vulnerable to cybercrime and face the most severe consequences. A study by Accenture reports that 43% of cyber attacks target small businesses, while only 14% are equipped with adequate cyber defenses.
Depending on the severity and scope of the cyberattack, it can have a serious and lasting impact on your company’s infrastructure.
In addition to financial loss resulting from cyber attacks, your business may also suffer from system downtime, damage to brand reputation, lost data and lost productivity.
For these reasons, it’s critical for businesses of all sizes to be cognizant of the impact that cyber attacks can have in order to minimize the consequences and prevent them from occurring in the first place.
Common Types of Cyber Attacks
Knowing the most common types of cyberattacks will help you develop a keen eye for suspicious activity so that you can act wisely to prevent theft and fraud.
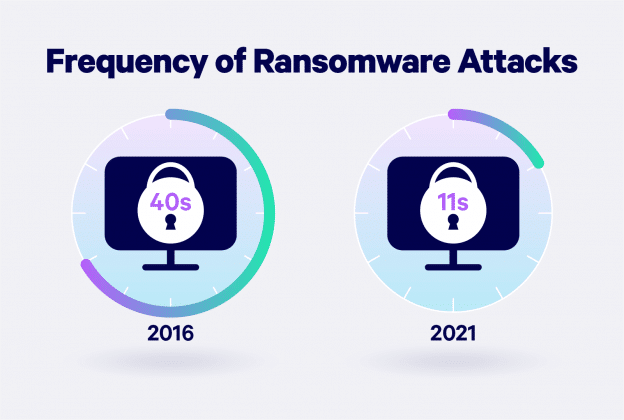
Ransomware attacks occur when malicious software is used to restrict access to a computer’s systems or data until a ransom is paid to the perpetrator. These attacks are becoming more prevalent and more advanced as technology evolves. In 2016, a business faced a ransomware attack every 39 seconds, but this is expected to rise to every 11 seconds in 2021.
2. Phishing
Phishing is a type of online scam that involves sending an email or other virtual communication impersonating a seemingly-reputable source, such as a bank or a government entity. These emails usually ask for personal information such as social security numbers to steal identities, money, or open new accounts in someone else’s name. An FBI report revealed a loss of $57 million in one year to phishing scams.
3.Malware
Malware is malicious software that gets downloaded onto devices without one’s consent. It can cause devices to crash or allow hackers access to computer activity and files. Malware is often downloaded onto devices when users are prompted to click on unsecure links. Statista has reported nearly 678 million malware detections in 2020, almost four times the number of cases in 2015.
4.Man-in-the-Middle
A man-in-the-middle (MITM) attack occurs when a user intercepts communication between two people, or between one person and a machine. For example, a hacker might guide a user into a fraudulent site that appears to be the user’s bank’s website to collect their data. According to Netcraft, 95% of HTTPS servers are vulnerable to these attacks.
5.Data Breaches
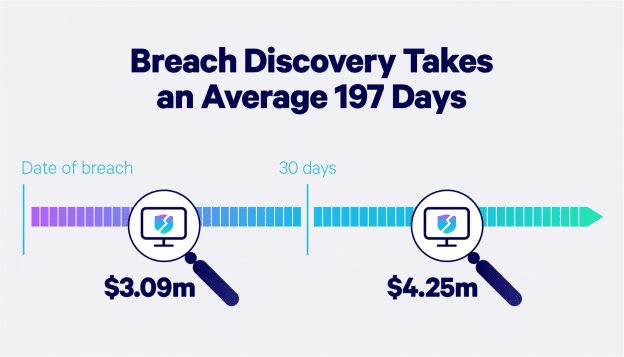
On average, it takes a company 197 days to discover a cybersecurity breach and up to 69 days to contain it. Needless to say, the longer it takes to discover a security breach, the more a company’s reputation and assets suffer. That’s why it’s essential for businesses to have a data breach response plan to be prepared if a breach ever occurs.
Industry-based Vulnerabilities
While it’s important for businesses in every industry to take comprehensive measures to combat cybercrime, certain industries are at greater risk than others.
It’s within expectations that companies in industries that possess users’ personal information are the most common targets of cybercrime. These industries include:
●Financial institutions. Not only do banks and credit unions have access to users’ personal information such as addresses and contact details, but they also manage financial assets and credit card numbers.●Healthcare institutions. Hospitals and other healthcare institutions safeguard sensitive patient data such as medical history, insurance information, and patient records.●Corporations. Corporations house not only data on employees and clients, but also the highly valuable intellectual property, product concepts, and contracts.
Cybersecurity Best Practices
With increasing cyber threats, especially due to the rise in remote work, businesses need to be as prepared as possible to mitigate the risk of cyberattacks. Here are some cybersecurity best practices that your company should follow to strengthen security and prevent cyber attacks.
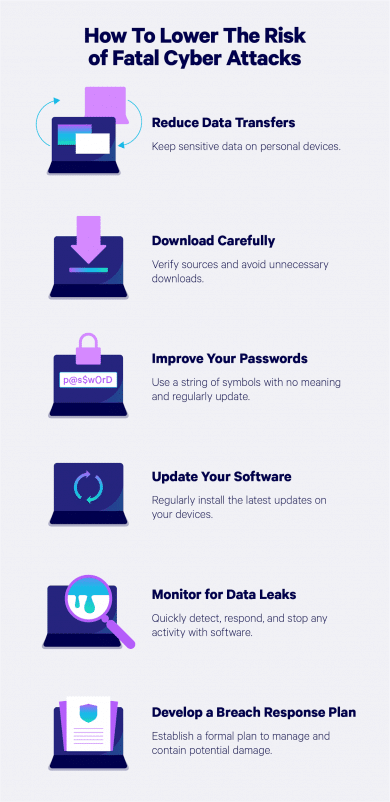
1.Minimize data transfers. In a corporate setting, it’s nearly impossible to prevent the transfer of data between devices. Be mindful of how many devices contain important data and try to make transfers as minimally as possible, especially when it comes to sensitive data.2.Verify download sources. Before making any downloads, scan the website you’re downloading from to ensure that it’s verified, and only click on legitimate download links.3.Update software regularly. Software developers are continuously updating their applications with the best available security measures, so updating your programs and devices whenever possible is a great way to protect against cyber attacks.4.Encrypt where possible. Encryption tools can be used to protect data from outsiders. When encryption isn’t possible, password protection is a great alternative. Be sure to choose complex passwords with a mix of letters, numbers, and characters, and to change your passwords regularly.5.Monitor data. Data breach monitoring tools will alert you when there is suspicious activity regarding your data. These tools will help you prevent data theft in real-time.6.Have a breach response plan. Breaches can happen to even the most prepared businesses. When they do, having a codified, organization-wide plan can help prevent further damage and speed up recovery efforts.
Cybercrime is becoming more frequent and more advanced every day, posing a threat to businesses and individuals everywhere. Rather than waiting to respond to a cyberattack, be proactive by bolstering your security measures to lower the risks of encountering an attack.