Security incidents have increased as criminals seek to take advantage of the coronavirus pandemic. The crisis has led to a surge in the number of cyber-attacks, malicious activities, and phishing scams, making cybersecurity awareness more significant than ever before for corporations, organizations, and other business entities.
In a bid to curb the virus, employers had to implement a work from home policy. The change in the working environment has provided hackers with new opportunities to exploit. Black-hats see remote workers as a weak link that can be utilized to gain access to corporate networks and steal sensitive information, install ransomware, or create backdoors. In this article, we’ll look at some of the basics of security awareness. We examine it’s fundamental for your remote workers during this period of the Covid-19 crisis.
What is security awareness?
According to Gartner, security awareness is a formal process of educating and training employees about IT. It involves:
- Programs on how to enlighten employees on cybersecurity
- Responsibility of every individual to upholding the organization’s security policies
- Techniques for auditing the effectiveness of the efforts
The first point is the basis of a security awareness program. However, it’s necessary to hold employees accountable and outline how you’ll measure the effectiveness of an organization’s security measures.
The process can be broken down into four stages;
- Determine the current awareness status within your organization.
- Crafting a comprehensive awareness program
- Implementing the said program
- Evaluate the program’s progress and come up with recommendations for revising what was not well executed.
Types of security awareness
-
Top-down awareness technique
It is not the employee’s responsibility to learn of the required code of practice or security best practices and apply them at work. It is the organization’s responsibility to train and educate its employees on matters concerned with security. From CEO to a part-timer, any employee can be an easy target if they are unaware of the potential for attacks and how they can succeed. Trickling this kind of knowledge from top executives eases the deployment process and ensures that every employee knows how to keep the company safe at their level.
-
Budgeting for awareness programs
One of the best indications of a company that is well-positioned security-wise for attacks is with a budget that covers security awareness. It shows how serious an organization is taking security compared to how funds have been allocated to other elements. If you are in a company that considers just sending email updates as security awareness, then you can be sure that you’ll be soon under siege.
Having a comprehensive security awareness program within your institution is just one piece of a reliable protection plan. Other primary elements of a viable protection plan would be:
- Creating a security policy
- Identifying vulnerabilities within your company
- Allocating resources to enhance security technology
However, security awareness is the most important. Companies should invest in security awareness just as much as they invest in software and other forms of security tech. No security tech will be successful if your workforce is an easy target for phishing attacks.
-
An organizational structure geared towards security awareness
This approach to security awareness is vital as it impacts everyone within the organization. More like the top-down approach, integrating an awareness program within an organization’s structure makes everyone’s job easier.
If possible, some employees should be exclusively tasked with implementing your security awareness program. At worst, there should be a single person responsible for the execution of this duty. Executives must give the team or individual tasked with implementing the awareness program full support.
-
Using a combination of different media to reinforce the message
We have covered the use of emails on sensitization about security a couple of times. They are excellent and can be adopted across the organization. However, you should have a blend of media forms to ensure that your company’s message about security awareness never gets ignored by the targeted persons.
For example, you can have internal workshops and talks within your organization about security. Afterward, emails may be sent and other short clips for communication through different media like instant messaging. Posters around the office may also work. The list of viable media forms goes on and on. The point is to make sure that the message is not complacent but is highlighted as very important.
-
Highlight recent attacks that hit news headlines
This is a very significant approach to security awareness. Ensure that you highlight all kinds of attacks and not only those that make headlines. This type of consciousness aims to show your employees how prevalent cyber-attacks are and how your system can be bypassed, and identify weak points that could be exploited within your organization’s infrastructure.
The best way is by finding attack news on companies of your size or those within your industry.
-
An awareness by cyber professional
For an organization with no security measures in place, going to a third party skilled in this area may serve the purpose. Competent experts will get you up and running and ensure that you recover the lost time. Even with comprehensive security awareness in place, it’s still necessary to bring an expert to check up and provide suggestions on what areas need improvement.
Security Awareness for Remote Workers during Coronavirus (Covid-19) Pandemic
More than ever, security awareness is now of utmost importance for your remote workers. It’s fair to say that the world has never seen more people working from home as it has during this crisis. Most companies have shifted their policies to help curb the spread of the virus. On the other hand, cybercriminals see remote workers as a weak link to gain corporate networks access and perform their intended malicious action.
An organization may have trained its employees on significant security concerns and cautions to take before the virus came to be. Most businesses may have given their employees security awareness training on risks they are likely to encounter, recognize various threats, and the best response for multiple threats. However, working from home due to this novel virus introduces many new risks and vulnerabilities that may not have been covered during the previous awareness training sessions. Also, regular training is necessary for remote workers, as risks increase when employees work from home.
In the section below, I’ll highlight some of the critical areas that MUST be addressed in work from home security awareness for remote workers.
Security Awareness for Remote Workforce is becoming a Necessity as COVID-19 Crisis Deepens.
SpamTitan, one of the leading email security solution providers, advocates for the use of robust layered technical defenses and email security solutions as we sink deep into this health crisis. However, despite how adequate the technical controls might be, they cannot stop all intruding inboxes’ threats. It might be tempting to put all your trust in technical security solutions. The truth is that, even with the best solutions in place, security infiltrations can still take place.
Several studies and research have highlighted the significance of providing security awareness to the workforce and the benefits that accrue in doing so. One such study conducted by KnowBe4, a security awareness training provider, uncovered that 37.9 percent of employees fail phishing tests if they have never gone through security awareness and social engineering training. A percentage that increased by 8.3 in the previous year. However, the figure dropped to 14.1 percent within 90 days after security awareness training to employees and phishing email simulations performed.
The volume of phishing emails and false campaign emails targeting remote workers have significantly increased during this Covid-19 crisis. Hackers aim at getting login credentials to SaaS platforms, emails, and VPNs through phishing campaigns.
Covid-19 was abruptly announced as a global pandemic, giving companies a concise period to strategize their adjustment plans. As a result, the rush to change from a mostly office-based workforce to a remote workforce might have seen security awareness training for employees put on a back burner.
However, the situation does not seem to be getting any better, with China experiencing the second wave of the virus. This implies that lockdown is likely to be extended for several months, and cyber-attacks targeting remote employees are bound to increase. Therefore, it’s essential to ensure that awareness training is provided to the remote workforce as soon as possible.
Increasing COVID-19 Domain Registrations and Web-Based Attacks
A comprehensive security awareness training for remote workers should also cover internet security as not all risks and threats will make it to the inbox. Hackers are evolving day by day and exploiting the new vulnerabilities being caused by the crisis. Phishing attacks used have a web-based component, and also, there are several malicious websites set up by black-hats for drive-by malware downloads. Most hackers currently use Novel Coronavirus and COVID-19 tricks to lure remote workers into downloading ransomware, malware, or access their login credentials for whatever corporate that’s being targeted.
An analysis conducted by Check Point Research revealed that approximately 42,000 domains related to Coronavirus and COVID-19 had been registered by the end of March 2020. And of the total number of those registered domains, 50 percent are likely to be malicious compared to other domains registered over the same period, as uncovered by Check Point Research.
It’s essential to raise awareness of the risk of using BYOD’s for corporate activities. There should be a limitation on what can be used to access the company’s website, standard security configuration for all BYOD’s within company infrastructure to be adhered to, and a list of websites that employees can access while using office devices. Above all, a security team should be in charge of identifying and blocking access to known malicious websites that hackers commonly exploit for fraud, distribution of malware, or phishing activities.
Shadow IT is a Major Vulnerability
For office-based employees connected to a corporates network, it is easy and more straightforward to identify the unauthorized software and hardware used by employees (Shadow IT). As for the remote workforce, it’s challenging to identify shadow IT, but the risk of malicious software being installed onto the device issued by corporate also increases.
Unauthorized software’s loaded onto corporate-issued devices carries a risk of malware infection and consequently increases attack-surface that hackers can easily exploit. IT teams have limited access and visibility into the unauthorized software. They cannot determine whether it’s running on the latest version and whether it has been patched against known vulnerabilities or not.
The ambiguity caused by shadow IT leads to several unidentified loopholes within a network infrastructure. It’s, therefore, significant to cover shadow IT in security awareness training for your remote workforce. Give them an in-depth explanation of why no software, apart from the ones listed in the company security policy, should be installed on a work device. Also, make them understand that they should seek authorization from the IT department on what USB devices or other storage devices can connect to corporate devices. Without such measures, the remote workforce may turn to be the weakest link in your organization during this pandemic.
COVID-19 crisis has seen most organizations turn to teleconference platforms to communicate with employees, partners, and other stakeholders. One of the most common teleconferencing platforms used by most organizations is Zoom. Research by some experts has shown some malicious installs of the genuine Zoom software but with malware bundled in it. Other installers have also been identified that install Remote Access Trojans, Coinminers, and adware that can be damaging.
Scammers Gaining from COVID-19
In recent weeks, we’ve seen several scams hit news headlines, with criminals seeking to take advantage of the public concerns, such as application for support due to school closure, reclamation of money lost during holidays, and so on. According to an analysis done by Google, scammers are sending 18 million Covid-19 related phishing emails to Gmail users in an attempt to steal sensitive data, lure victims into downloading malicious software’s or donate to vague causes.
Fake domains related to COVID-19 by April 2020
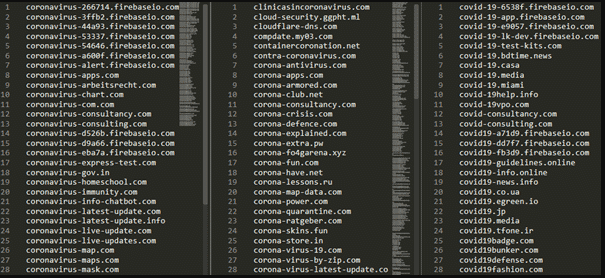
Recent campaigns have also seen cybercriminals mimic legitimate authorities such as HMRC and World Health Organizations through fake emails and websites to compromise targeted accounts, infect devices with malware, and steal confidential information. Scams promising to offer advice about financial support, how to access personal protective equipment, how to avoid being infected, and those providing updates about the virus have been the most prevalent in the recent past. Research has shown that the click rate of phishing attacks has increased from less than 5 percent to over 40 percent due to hackers’ tricks of provoking users’ fear and curiosity and encouraging them to respond promptly.
In most cases, hackers start the campaign through social engineering, through the following scenarios with a call for action coming in later stages of the organized cybercrime;
- Acquisition of fake products such as vaccines, medicines, and masks.
- Opening accounts in malicious websites
- Installing malicious android software and applications which creates backdoors for hackers to access your device or network. The apps help to bypass the 2-factor authentication mechanism meant to secure your system and accounts.
- Malware installation on devices, Windows in most cases. Various have been noted during this COVID-19 crisis, such as the infamous Emotet and Ryuk ransomware.
Various ongoing campaigns using the COVID-19 template
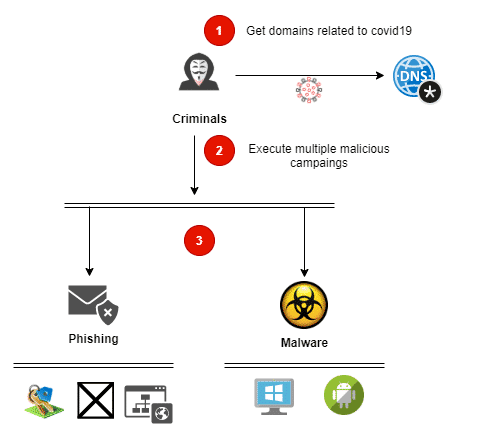
From phishing to malware
Emotet and Trickbot have been the most prominent “winners” during this pandemic. Hackers have used this malware to reach a higher number of victims using COVID-19 templates. Cybercriminals encode the victim’s data and demand a ransom.
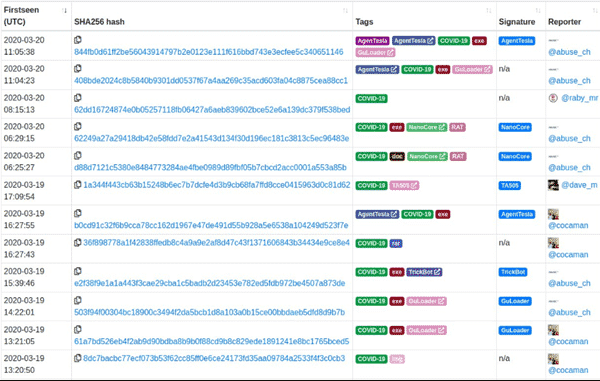
Abuse.ch shows, from a global perspective, how COVID-19 templates are bundles with other common threats. Different malware samples, such as HawkEye, AgentTesla, Formbook, NanoCore, and MetaMorfo, have been used.
A list of malware with Coronavirus template
Currently, malware attacks on Android devices pose as one of the most challenging scenarios for organizations with many remote workers. The modern attack techniques have infection rates that are far superior to traditional techniques.
Attacks that have occurred in the recent past takes place in two steps;
- The target is convinced to download a COVID-19 tracker or any relevant COVID app outside the Google Play store.
- After it has been installed, the malware takes over control of the device and then demands about 100 USD in Bitcoins.
Therefore, companies, organizations, government institutions, and other work-from-home employees should invest heavily in employee security awareness.
Employees currently working from home should think three times before clicking that link or downloading that software onto your BYOD. Yes, it might take you less than 20 seconds to click the link, but a lifetime to recover from the damage caused.
Beware, take caution always!
Share on Facebook
Facebook
Share on twitter
Twitter
Share on linkedin
LinkedIn
Share on mix
Mix
Share on pinterest
Pinterest
Share on tumblr
Tumblr