Cybercrime has become a major concern for businesses of all sizes. The growth in data breaches, ransomware (malicious software designed to block access to a computer system until a sum of money is paid) attacks and acts of cyberterrorism is unprecedented. According to recent data, the incidence of such cyber attacks has seen a surge in the past few years. These malevolent activities are persistent and show no signs of relenting.
Key examples of such cyber threats include malware (any software intentionally designed to cause damage to a computer, server, client, or computer network) strains like ZCryptor, Petya, and WannaCry. These sophisticated security threats have caused significant financial and reputational harm globally. Numerous reports detail their destructive impact, underlining the realism of these threats.
A noteworthy point is that the internet's insecure architecture often contributes significantly to the proliferation of such threats. Furthermore, the existence of professional hackers, who develop harmful tools that can potentially fall into the wrong hands, further amplifies this problem.
Regrettably, many organizations still adopt a reactive rather than a proactive approach to these security issues, making them more vulnerable to attacks. As such, the discussion on the need for quicker adoption of adequate security measures is more critical than ever.
Cyber threats pose serious risks to organizations and individual users alike. Instigated by malicious actors, these risks include malware attacks, which aim to infiltrate and cause havoc within computer systems and networks. Disconcertingly, malware is not a singular entity but instead a composition of different harmful computer programs such as viruses, trojans, ransomware, and spyware.
Some may ask, what exactly is malware? In simpler terms, malware is any software intentionally designed to cause damage to a computer, server, or network. The increasing number of mobile malware variants has made it easier than ever for cyber criminals to launch devastating attacks.
For instance, the encryption-based malware known as ransomware can paralyze a whole organization by denying access to crucial systems and files, forcing businesses into paying hefty ransom fees. Meanwhile, spyware stealthily collects and shares sensitive personal information without the user's knowledge.
The threat landscape also includes viruses and trojans, which can replicate inside systems causing a myriad of issues including alteration of computer functions and unauthorized distribution of malicious programs, respectively. Real-life examples are abundant, with countless instances of organizations falling victim to these cruel tactics, often resulting in huge financial losses and stolen intellectual property.
However, not all hackers are cybercriminals. Ethical hackers, for instance, utilize their knowledge and skills to bolster system defenses and aid in the extraction of potential vulnerabilities, making them an asset in the fight against malware.
Preventing and combating cyber threats require a multi-pronged approach, including strong security infrastructure and vigilance against suspicious activities. Equally essential is the education of employees and individuals about possible threats and how to respond.
On an ending note, while the world of cyber threats might seem intimidating, it's important to remain informed. Ultimately, comprehension and vigilance form the foundation of cyber defense.
So, what is ransomware? It's a type of malware that encrypts a victim's files and systems, blocking their access. The attacker then demands a ransom to restore this access. Imagine a kidnapper holding your data hostage and asking for a ransom - that's ransomware for you. It's one of the many forms of cybercrimes that pose significant threats to organizations.
And what about the broadly mentioned term malware? It refers to malicious software including viruses, worms, and trojans, that hackers use to gain unauthorized access to systems and data. Detrimental to computers, servers, or networks, malware is a common tool in the cybercrime arsenal.
It's evident that cyber threats are real and evolving. As digital citizens, it's crucial that we stay informed and adopt practices to secure our platforms. As for businesses, it's time they prioritize strengthening their cybersecurity to protect their data and systems from such threats.
Given the dramatic increase in cybercrime incidents, it's clear that we need to ramp up countermeasures. It's not just a theoretical threat - it's happening, and the statistics back it up. So let's get proactive about cybersecurity!
In light of the rising rate of cybercriminal activity, companies are finding themselves more vulnerable to cyber threats, thanks to the widespread adoption of innovative digital technology. Critical sectors are particularly prone to these threats as they rely heavily on these modern technologies, providing a bigger payoff for criminals successful in their cybercrime exploits. A surge occurs in global cybercrime due to many factors, which needs addressing.
Unprecedented growth in digital technologies, for instance, has made it easier for advanced hacking tools to be developed, contributing to the escalation of cybercrime. This includes the noteworthy 54% surge in the variations of mobile malware, adding to companies' growing concerns. Furthermore, critical sectors' utilization of digital technologies covers both vital processes and significant assets and infrastructure, broadening the potential targets for cybercriminals.
Given these trends, it is crucial that organizations take concerted actions by adopting intensive security measures to negate these threats. It is not enough to just know about the digital threats; it is equally important to provide tangible examples and actions for combating these threats.
Organizations should consider implementing secure digital protocols, regular network testing, and employee cyber security training. This strategy aligns with recommendations to enhance slower security measure uptake, and can effectively mitigate potential cybersecurity threats.
Without doubt, the proliferation of digital technologies has been beneficial to the advancement of industries, but with it, comes the shadow of ever-evolving cyber threats. Hence, it's utterly crucial that we understand the reasons behind the rapid rise in cybercrime and proactive steps are undertaken by organizations to protect their vulnerabilities from such malicious cyberattacks.
Explaining Prevalent Cybercrimes Today
In our increasingly digital world, we are confronted with a variety of cybercrimes that represent a threat to our security. Here, we delve into a group of widespread cybercrimes, each intricately linked to the insecure Internet architecture or activities of unethical hackers as detailed previously. We will cover common offensives such as identity theft, phishing, hacking, cyberstalking, among others, providing context on their emergence and operation.
Identity Theft
Identity theft is a prominent cybercrime where hackers steal personal information to impersonate the victim, often for financial gain. The insecure Internet architecture discussed earlier largely facilitates it.
Phishing
A prevalent cybercrime, phishing involves sending deceptive emails or communications to gain sensitive data such as passwords or credit card numbers. This crime demonstrates the potentials of unethical hacker activities outlined before.
Hacking
Hacking refers to unauthorized access to networks or computers, often enacted by those unethical hackers or poor Internet security we mentioned earlier.
Cyberstalking
A criminal act that has risen with digital progression, cyberstalking involves harassing or threatening individuals online—yet another crime easily committed thanks to insecure Internet architecture and hacker activities.
Quantifying the above points, statistics indicate a steep rise in cybercrime incidents, highlighting the urgent need for preventative action. Therefore, it is crucial to connect these cybercrimes to the reasons stated in the summary, amplifying the need to tighten Internet security and tackle unethical hacker activities.
Cybercrime encompasses all illicit activities that engage or target a device connected to a network, or a network system itself, and the broader Information Technology (IT) infrastructure. When we say "networked device", we mean any gadget or piece of equipment that is connected to a network to either share or receive data or resources. IT Infrastructure, on the other hand, refers to the comprehensive collection of hardware, software, networks, data centers, facilities, and related equipment used to develop, test, operate, monitor, manage, and/or support Information Technology services.
The focus of these criminals, more commonly known as cybercriminals, is to use computer technologies to conduct illegal activities. These actions can range from identity theft, infringing upon one's personal privacy, to carrying out operations linked to unauthorized distribution of intellectual property and child pornography.
Cybercriminals exploit vulnerabilities present in digital systems to conduct these attacks. Let's examine a real-life example to illustrate how they utilize these system weaknesses for their ill-intent. Imagine an average person using their smartphone to log into their online banking account while connected to a public Wi-Fi. Cybercriminals, lurking on the same network, can easily intercept this data transfer and with the right set of tools, decode the person's login credentials. They then have complete access to this person’s bank account and can conduct transactions without the person even knowing.
In the last decade, data shows that the instances of such cybercrimes have increased exponentially, highlighting the alarming significance and global impact of the issue. The advent of mobile malware, a software specifically designed to harm, disrupt or gain unauthorized access to mobile devices, has also dramatically contributed to this surge.
While cybersecurity measures continue to advance, they are often met with even sophisticated hacks and breaches. This highlights the serious and ever-evolving nature of cybercrime. To fight back, organisations employ ethical hackers who, unlike cybercriminals, use their skills to detect vulnerabilities and patch them before they can be exploited. Therefore, not everything relating to hacking is inherently malicious; it’s the intent that matters.
As technology continues to evolve, so do the methods and channels through which cybercriminals carry out their illicit actions. This constant game of cat-and-mouse between cybercriminals and cybersecurity experts underlines the critical importance of maintaining robust digital security measures to safeguard our information and digital assets on the Internet.
In conclusion, understanding the workings of cybercrime and the threats they pose allows us to appreciate the importance of pentesting and why organizations invest in hardened cyber defenses.
Given below are some of the most frequently witnessed forms of cybercrime that exemplify the ever-growing risks mentioned in the foregoing rationale: 1) Identity Theft: Such a crime occurs when delinquents hack into personal e-mails or internet banking portals to pilfer personal data and conduct fraudulent activity in the name of the individual whose data they have stolen. 2) Cyber Stalking: This form of crime consists of using the internet or other digital forms of communication to torment an individual, group, or institution. 3) Phishing: Cyber attackers using this method dupe individuals into exposing their confidential information, including security codes and credit card numbers. 4) Malware Attacks: These are the attacks that relate to software manufactured with the intent to harm or put out of action computers and computer systems.
1. The Expanding World of Identity Theft in Cybercrime
Identity fraud is an ever-growing concern in the digitized world, with its tendrils reaching far into various aspects of cybercrime. This section sheds light on how Identity theft proves to be a major culprit in escalating cybercrime rates. We delve into insightful examples, shocking statistics and useful knowledge about Identity Theft, underlining its impact and significance within the realm of cybercrimes. Stay tuned to understand more about this crucial topic and enhance your awareness.
"Identity theft" is a devious form of scamming where offenders utilize another individual's identification credentials for malicious purposes. This may involve hackers who have unauthorized access to an individual's banking or credit card details and manipulate such information for stealing funds or making arbitrary purchases in the identity owner's name.
One aspect that this section could delve deeper into pertains to the factors contributing to the exponential surge in cybercrimes, as indicated in the article summary. For example, the insecure architecture of the internet is a major factor that predisposes personal data to potential theft. The proliferation of mobile malware is another catalyst that significantly amplifies these breaches.
Moreover, the relative slowness with which companies adopt robust security measures makes identity theft easier. It would be beneficial to underscore which of these aspects are more implicitly related to identity theft. The narrative could further encompass the particular tools employed by delinquents for stealing identities as referenced in the summary.
In addition, there is a need to draw a clear distinction between miscreants who pilfer identities and ethical hackers who are instrumental in fortifying security systems. It would also be productive to highlight continuous malevolent campaigns by cybercriminals, and the way they exploit security loopholes to their advantage.
Identity theft, although not a novel concept, has gained substantial momentum in the digital age. Today's technological advances have made it alarmingly easy for identity thieves to pilfer valuable personal information. Online transactions, a necessity for many in today's world, have become a breeding ground for such treachery, with perpetrators deploying various techniques like annoying ad pop-ups, intrusive spam emails, and deceptive phishing attacks.
However, identity theft is not limited to these well-known tactics. It encompasses a wide range of deceptive practices that extend beyond spam emails and phishing attacks. For instance, criminals sometimes target major companies, exploiting weak security measures to obtain customer information on a mass scale. These incidents, often making headlines, underline the severe and growing threat of identity theft.
The statistical data further underscores the gravity of the situation – millions fall prey to identity theft each year, leading to billions of dollars in losses. This paints a bleak picture of the digital landscape and emphasizes the urgent need for robust security measures.
Factors contributing to the rise of cybercrimes like identity theft include the inherent vulnerabilities of internet architecture and the slow adoption of comprehensive security measures by organizations. Focusing on these aspects could provide insights into why we have seen a proliferation of identity theft in recent years.
The fight against identity theft doesn't have to be a losing battle. Everyone has a role to play in safeguarding personal information. Reliable preventative steps, which will be explored later in this article, can drastically reduce your chances of becoming an identity theft victim.
At the end of the day, understanding the nature of identity theft is a vital step in its prevention. By making sense of its mechanisms and scale, people can take informed steps to protect themselves from becoming a statistic in this expanding realm of cybercrime.
An understanding of cybercrime deepens when we consider a few notorious examples like massive data breaches or notorious hacking incidents. Such instances drive home the point about the harsh reality of cyber threats. They also highlight the intricacies of different types of phishing scams and how they contribute to the increasing proliferation of cybercrimes.
Moreover, understanding the fallout from clicking on a phishing link can be eye-opening. It's not just a simple click; it's the key that opens the door to your personal and financial information, putting you at risk.
Imagine being at the heart of a thrilling true crime story, where every click could mean the difference between security and a shocking reveal of your personal information. That's the world of online security, where the hunt for safety is a suspense-filled journey. Stay vigilant, stay safe.
Understanding the Threat of Phishing Scams
Phishing scams are a primary tool in the criminal cyber world. These scams are best understood by breaking down what they entail and how they ensnare unsuspecting individuals. Knowledge of why phishing is a preferred method among cybercriminals deepens your understanding of our previous discussion on cyber threats.
Phishing scams employ numerous techniques to deceive their victims. Recognizing these common strategies is vital in protecting yourself from such threats. Therefore, let's delve into some details of these techniques and explore why they work so effectively.
The risks involved in falling prey to these scams are tremendous. Expanding on the potential dangers and the extreme consequences of phishing scams helps believers grasp the severity of these threats. Prepare to receive a jolt of reality as we expose the dark consequences that may follow a successful phishing scam.
Arm yourself against these cyber threats by learning a few simple and practical tips on how to identify and avert phishing scams. Equip yourself with knowledge and stay one step ahead of these cybercriminals.
Online fraudsters deploy phishing tactics as an easy, yet extremely successful, method to deceive their targets into disclosing sensitive data, such as their banking credentials, social security data, and further forms of private information. The growth of phishing scams showcases how fraudsters can successfully exploit victims with limited resources at their disposal.
Part of why phishing attacks are increasingly prevalent has to do with the bigger picture of growing cybercrimes. For instance, driving factors such as the insecure foundation of the internet architecture make phishing scams much easier to execute. Additionally, cyber threats get a helping hand when criminals misuse the efforts of ethical hackers for nefarious phishing operations.
Let's delve deeper and assess the implications of falling for these scams. Falling prey to phishing can lead to catastrophic outcomes, such as significant financial losses, identity theft, and breaches of personal privacy. These consequences can be severe, causing lasting damage to a person's life.
In order to contextualize the issue, let's consider the well-known phishing fraud carried out by the "Prince of Nigeria". Victims received emails claiming that they were part of a significant inheritance. All they needed to do to claim it was to provide their banking information. A multitude of people fell for this notorious scam, reinforcing the need for awareness.
Readers must take precautionary measures to safeguard themselves from phishing attacks. A good starting point can be embracing security practices that are typically slow in adoption, such as two-factor authentication and regularly updating passwords.
The adeptness of cyber fraudsters can make them appear ordinary and unthreatening. However, don't be fooled. The victims of these insidious scams can attest to the contrary. The best way to protect yourself is by staying informed and implementing robust safety measures.
In conclusion, one should not underestimate the damaging potential of phishing scams. By understanding their modus operandi and maintaining strict vigilance, we can prevent these attacks and safeguard our vital information.
Hackers can create a phishing website, which mimics a real website to trick users into providing sensitive information. Criminals may also send email messages in bulk containing links to malicious websites or attachments, hoping that users will click them.
Exploring the Depths of Malware Attacks
Diving into the topic of malware attacks, we aim to expand your understanding of their complexities. We'll decode how they materialize, spotlight the tactics employed by cybercriminals, and reveal the potential outcomes of such incidents.
By illustrating well-known malware cases, we hope to articulate just how severe and widespread these attacks can be. More than just a simple briefing on their history, our objective is to offer a clearer picture of the gravity these acts of cyber crime hold.
While the subject can be complex, we'll break down how cybercriminals sneak in malware, and arm you with the knowledge to spot any red flags that could point to an ongoing attack.
We believe knowledge is only as useful as its application. So, we won't stop at merely discussing malware attacks. Our commitment is to empower you with strategic, industry-recommended countermeasures you can apply to fortify your cyber defenses and safeguard against such threats.
Malicious cyber actors use malware attacks to infect a computer network or system with viruses, trojans, ransomware, and spyware. Malware is any program developed to harm a computer. A malware infection can enable cybercriminals to compromise an organization and steal highly confidential information, such as intellectual property and competition strategies.
Cybercrime is a serious issue today, and a significant contributor to this problem is malware. Malware, or malicious software, encompasses a variety of harmful computer viruses, worms, trojans, and other damaging programs. The purpose of these programs is to enable unauthorized access to systems and data, often leading to significant damage.
Among the various types of malware, one particularly prevalent and damaging strain is ransomware. Ransomware is a unique type of malware, possessing the power to encrypt a victim’s files and systems. The cyber attackers then hold the victim's data ransom, preventing them from accessing their own files. Only upon payment of the ransom does the perpetrator release them or provide a decryption key. This ruthless method exemplifies the growing threat of cybercrime.
A notorious real-world example of a ransomware attack and its devastating impact is the global WannaCry attack. Cybercriminals used this ransomware strain to infect thousands of computer systems worldwide, showcasing its destructive capabilities.
However, ransomware represents only one piece of the vast malware puzzle. There exist myriad other types of malware, each with unique impacts and threats. By understanding the various forms of malware and the potential damages they can cause, we can better protect ourselves from falling victim to these cyber threats.
Ensuring we are educated on this topic is of paramount importance. The slow adoption of advanced security measures and perpetual cyber campaigns further emphasize the need for awareness and understanding. Avoiding redundancy in our information and providing clarity on different threats are crucial steps in combating cybercrime.
Understanding and Combating Distributed Denial of Service (DDoS) Attacks
Unpacking the concept of Distributed Denial of Service (DDoS) attacks can shed light on why these techniques are often the weapon of choice for cybercriminals. Essentially, DDoS attacks overwhelm a system's resources, making it virtually inaccessible to its legitimate users. The immediate consequence of such a hit is severe business disruption, but one can't underestimate the potential financial losses either.
With the cybercriminal terrain constantly morphing, methods like DDoS are becoming increasingly popular. A key factor in this trend is the automation of cybercrime, which allows for the execution of large-scale attacks with little to no human intervention. Moreover, the internet's inherently insecure architecture continues to be a breeding ground for vulnerabilities ripe for exploitation.
Further adding fuel to the fire is the misuse of legitimate hacking tools to carry out nefarious operations and the slow adoption of strong security measures across the board. The proliferation of sophisticated malware and ongoing malicious campaigns also contribute to the high incidence of DDoS attacks.
So, what's the defense against these high-tech, low-faith hits? Guarding against DDoS attacks requires a robust security posture, complemented by up-to-date knowledge about evolving threats. Every effort should be made to minimize the potential impact of DDoS attacks. Remember, the tie between DDoS attacks and the aforementioned factors is intricate, but understanding it can be a game-changer in safeguarding against potential threats.
DDoS attacks are a tool for cyber adversaries looking to disable organizational networks and computer systems. These attacks occur when hackers inundate a company's network with excessive traffic, effectively denying access to authorized users trying to utilize network resources. It's like a crowded entrance door, where the genuine guests can't get in due to the rush. Even worse, the reason this surge in traffic happens is that the system is bombarded with numerous connection requests, which is similar to the way DDoS attacks work.
DDoS attacks form a critical part of the ever-growing cybercrime phenomenon. This growth has been spurred on by factors such as the inherently insecure architecture of the internet and the slow adoption of robust online security measures. Networks with poor security are like low-hanging fruits for attackers and are thus more susceptible to these assaults.
Lamentably, businesses often delay upgrading their security systems until a severe security breach occurs. Their hesitation aids cyber adversaries in their malicious activities and acts as a catalyst for cyberattacks like DDoS. Strenuous attempts to understand DDoS attacks, therefore, are elemental to understanding the broader issue of proliferating cyber offensive campaigns. Our network’s safety starts by acknowledging the threats we face.
It is common for malicious cyberagents to engage in tactics known as DDoS attacks, an acronym for "Distributed Denial of Service". The goal of such a strategy is to flood a website or online service with so much traffic that it cannot function properly, essentially blocking regular users out. A common purpose of these DDoS attacks is cyber-extortion, where the cybercriminal threatens to unleash a DDoS attack unless a hefty ransom is paid. However, another darker, more devious use of DDoS attacks is as a smokescreen to carry out other forms of cybercrime unnoticed.
Data from cybersecurity firms reveal a troubling increase in these types of attacks. The number of DDoS attacks, for instance, has risen dramatically over the last few years and the financial damage they cause is alarming. Such impacts underline the need for more proactive cyber security solutions and public awareness.
A case in point is the 2017 DDoS attack that brought down the U.K. National Lottery Website, rendering its website and mobile application inaccessible. This led to a significant disruption for the online lottery players. However, the attack wasn't merely about disabling the lottery site. Investigations revealed that the DDoS assault was actually a distraction for a more sinister operation where sensitive data was being targeted. This incident serves as a vivid illustration of how DDoS attacks are not isolated incidents but part of a deeper issue in cybercrime today.
In conclusion, it's essential for us to understand DDoS attacks and cyber-extortion tactics in all their complexity, as this understanding is a key part of the larger struggle against rising cybercrime trends.
Recent Cybercrime Statistics and Trends: Unpacking the Rapid Expansion
In the rapidly changing digital landscape, cybercrime has become a hot-button issue. In this discussion, we delve into six root causes behind the alarming expansion of cybercrime, backed with recent statistics to lend credence to our arguments.
Rising Incidences of Cybercrimes
Anecdotes are no longer enough. The latest data indicates a significant escalation in the number of cybercrimes, confirming that this issue is not just theoretical but an urgent reality.
Use of Advanced Cyber Tools by Criminals
A parallel growth factor is the increased accessibility and sophistication of cyber tools meant for malicious activities. The figures demonstrate a sharp and worrisome rise.
Insecure Internet Architectures
The proportion of compromised internet architectures is also an enabler of cybercrime. Recent statistics underpin this, pointing to an urgent need for more secure systems.
Epidemic of Ethical Hackers Versus Malicious Actors
Unfortunately, the number of ethical hackers is lagging behind malicious actors. Data on this vast gap underlines the need for more investment in ethical hacking.
The Growingly Outdated Security Systems in Big Companies
Despite what we'd like to think, even large corporations are not necessarily safe. The frequency of system updates in these companies needs to increase, as recent statistics tellingly reveal.
The Evolution of Mobile Malware
As our dependence on mobile devices has grown, so has the rate of mobile malware variants. New data suggest a spike in their manufacture and distribution.
Frequency of Malicious Campaigns
Lastly, the frequency of malicious campaigns is yet another statistic that adds to the complexity and acceleration of cybercrime.
Armed with these statistics, it is our hope to shed light on the scourge of cybercrime, encourage informed discourse, and ultimately contribute to the development of robust solutions. Each statistic cited is fetched from reputable and reliable sources, ensuring the accuracy and authority of our discussion.
The rise in cybercrime threats over the past few years is staggering, as evidenced by numerous reports and studies. Yet, the crucialness of cybersecurity does not seem to resonate with a significant number of individuals and organizations. Many continue to employ overused identifiers to secure their devices and accounts, while others persist with devices deficient in proper security features.
This careless approach raises severe concerns, as it inadvertently aids the growth of cybercrime. The rampant use of generic or easily decipherable credentials, coupled with the lack of robust security measures on devices, intensifies the potential damage each cybercrime can wreak.
Indeed, real-life incidents yield a clear picture of the consequences of weak cybersecurity measures. From identity thefts to large scale data breaches, the repercussions of lax cybersecurity efforts are far too devastating to be overlooked. Therefore, the necessity for thorough and proactive cybersecurity implementations cannot be stressed enough.
Cybercrime is a growing threat, with certain statistics emphasizing just how dire the situation has become:
Experts have noted an unprecedented surge in cybercrimes over recent years. For context, consider the dramatic increase in cybercrime rates that have been noted across numerous studies, clearly showcasing a worrying trend.
The internet's broad-reaching architecture is constantly under threat, and studies reveal startling numbers regarding its insecurity. These statistics highlight just how prevalent this issue is, and why it's a point of concern.
The ratio of ethical hackers to criminal hackers is another consideration. Data suggests both a rise in the hacking community but also an increase in those using their skills for ethical hacking purposes. This balance is something to be aware of when discussing cyber security.
Many businesses don't practice adequate security measures until a problem arises. This can be seen in studies and statistics that show companies delaying the adoption of solid security measures until faced with a direct threat.
Mobile malware variants are another issue. As more people use mobile devices, the number of mobile-related cybercrimes is rising alarmingly. Figures indicate an increasing proliferation of mobile malware, which adds another dimension to the cybercrime landscape.
And despite recognition of the problem and steps taken to mitigate these risks, malicious campaigns persist. The numbers indicate an unfortunate reality: these damaging schemes continue at a high rate, even in the face of odds stacked against them.
All of these points help paint a vivid picture of why cybercrime is such a critical threat worth paying attention to.
1. Cyberattacks occur every 39 seconds: According to a study conducted by the University of Maryland, a threat to our digital security surfaces every 39 seconds. This may manifest itself in the form of a phishing or a malware attack, or an instance of hacking.
Cyber threats are commonly attributed to the inherently vulnerable architecture of the internet, which provides a near-perfect field for these repeated attacks. Despite the extent of cyber-attacks, the adoption of strong security measures has been slow, contributing to the continual onslaught of attacks. In addition, the surge in mobile malware variants has made handheld devices a prime target for cybercriminals.
These threats, such as phishing and malware attacks, are not just mere inconveniences. They can cause significant harm, ranging from theft of sensitive personal information to the shutdown of entire computer systems or networks. The high frequency of attacks underscores the importance of understanding the different forms of cybercrimes and implementing measures to protect oneself from becoming a victim.
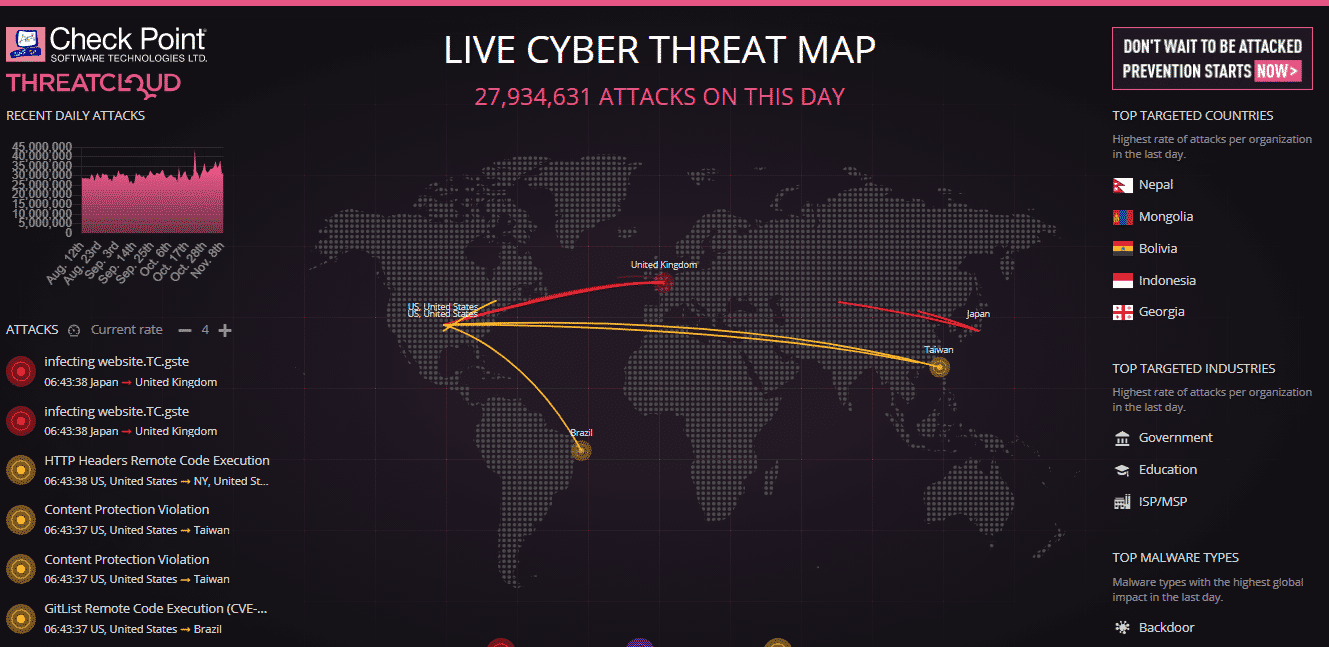
The alarming extent of cybercrime becomes terrifyingly clear when visualized via a real-time threat map, courtesy of Check Point Software Technologies. This map chillingly details over 27 million cyberattacks that occurred within a single 24-hour period. Graphics like these serve as a sobering cautionary tale about the extensive impact of cyber offenses being persistently executed worldwide.
Such astronomical figures emphasize the critical importance of implementing dynamic cybersecurity strategies. Whether an individual, corporation, or government entity, the stark data reminds us of the relentless digital threat landscape we all face. Furthermore, it draws attention to how cybercriminals are not just using cutting-edge technology but they are also benefitting from existing vulnerabilities in our digital infrastructure. They prey on these weaknesses to compromise a plethora of devices and networks, thereby intensifying the cybercrime threat landscape to unprecedented levels.
2. Almost 80% of U.S. firms have fallen prey to cyberattacks: It's no surprise that cybercriminals often target corporations with access to sensitive personal or financial information - the lure of financial profit is simply too great. This risk disproportionately affects small- to medium-sized businesses (SMEs) due to their limited resources for implementing comprehensive cybersecurity measures. As these businesses comprise the majority, they also end up becoming the prime targets and victims of cybercrimes.
Dwelling deeper into the statistics, we find that such a high proportion of U.S. organizations falling victim to cyberattacks is not a random occurrence but an alarming trend. Reports by trusted research outfits substantiate this, underlining an upward trend in cybercrime over recent years.
Given the emphasis on SMEs, we must highlight what makes them so vulnerable. Limited budget, inadequate cybersecurity infrastructure, and a lack of understanding about potential threats often play against them. As the stakes for these businesses are high, understanding their susceptibilities can shed light on the severe repercussions of such breaches.
Furthermore, it's crucial to clarify why cybercriminals typically target SMEs. Is it their inadequate cybersecurity policies, budgetary restrictions, or underdeveloped security infrastructure? This explanation would provide a holistic understanding of the situation.
Connecting this with the slower adoption of robust security, we underline the necessity for refined and proactive cybersecurity strategies. Unattended security loopholes can open doors for cybercriminals, costing businesses exponentially. Hence, companies, especially SMEs, should recognize the importance of strong security measures against potential cyber-threats.
Finally, if we revisit our understanding of 'cybersecurity', we can see why these implementations are critical for every business size. Having a strong security framework is more than just prevention; it is maintaining the sanctity of information and systems against unauthorized access.
Understanding the ticking time bomb that is cyber-risk, we hope to emphasize the urgency of the matter. Without swift and adequate action, more businesses will continue to fall victim to cybercrime.
3. Understanding the Importance of Hackers in Maintaining Information Security
In order to better understand the concept behind the role of hackers in information security, it is key to first clearly define some terms. Particularly, terms such as 'security researchers' or 'ethical hackers' must be explained in a manner that allows those who are not familiar with cybersecurity jargon to easily grasp their meanings.
Sometimes, to truly comprehend a concept, it helps to look at real-life examples. Our discussion regarding hackers in information security can be augmented by including a brief study or an anecdotal scenario. This will highlight how ethical hackers, in the past, have identified and rectified security vulnerabilities, thereby aiding in the fight against cybercrime.
In our earlier summary, we mentioned 'legitimate hacking tools'. It is time to delve deeper into this. We will discuss these tools in more detail, focusing particularly on how they can be misused by cybercriminals. Moreover, we will reveal the techniques that security professionals employ to prevent such misuse.
One key aspect of anything cyber-related is it is forever evolving. New strategies are being developed by hackers, making it all the more necessary to keep our content current with the latest trends. Let's take a look at these new strategies and understand how they are shaping the world of cybercrime today.
Finally, to conclude this section, it would be beneficial to recommend some practices for hiring ethical hackers or 'security researchers' within an organization. These recommendations can outline what type of vulnerabilities to be wary of and what precautions should be considered with regards to ethical hacking. By elaborating on these points, we hope to provide a comprehensive understanding of hackers' role in information security.
Take for example, the Sharp increase in Trojans and Ransomwares reflected in the heightened activity of cyberattacks over recent years. These malware variants can cause immense damage to systems, from theft of personal data to complete system lockdown. According to a 2020 report, there was a 60% increase in affected users just over the course of a year.
As technology advances, it is clear that the threat of mobile malware is becoming more prevalent. Everyone needs to keep up to date with the different types of malware and stay informed about the best ways to protect their devices. One effective strategy is regular system updates, as these often include patches to known security vulnerabilities. Following good practices when it comes to downloading apps and software is also vital – only download from trusted sources, and double-check permissions and access requests from apps.
With informed actions and preventative measures, we can all help to lower the risks associated with mobile malware. Always ensure that the information you are using and sharing is the latest and secure, as the sphere of cybersecurity is incessantly improving.
4. Challenges and Opportunities in Adopting Enhanced Security Measures for Companies
It's no secret - the journey towards adopting robust security measures can be an arduous one for many companies. But why is this so? The reasons are multilayered, and primarily involve aspects such as cost implications, time constraints, and a pervasive lack of knowledge about cybersecurity.
Expanding on these hindrances, it's important to note that integrating advanced security systems is a financially intense process that not all businesses can afford. Additionally, the time required to implement, test, and fine-tune these systems can also be a deterrent. But perhaps most daunting of all is the software knowledge gap that exists in many companies, a hurdle that can lead to hesitations and delays.
However, the consequences of delayed security upgrades can't be ignored. Take, for example, the numerous companies that have suffered extensive damages as a direct result of poor security systems. These incidents, though unfortunate, serve as a pressing reminder of the broader implications of a lax security framework. The impact extends beyond the company walls, distressing clients, impacting the economy, and opening doors for cyber-terrorists.
On a more encouraging note, the journey towards robust security need not be all gloom and doom. There are a myriad of potential solutions that companies can adopt to navigate these obstacles. The key lies in balancing the negatives with positive and proactive steps. This could mean investing in security awareness training, or even incorporating best practices like encouraging strong password use and regularly updating software systems.
Adopting robust security measures is more than just a company responsibility - it's a crucial cornerstone that determines the safety of our economy and society. The road might be challenging, but with the right strategies in place, enhanced security can become an attainable goal, rather than an insurmountable hurdle.
The consequences of these breaches can vary widely depending on the particular security flaws that were exploited. This points to the urgent need for a more nuanced and comprehensive understanding of the data security landscape - something that companies are yet to fully grasp. Many businesses are now considering various strategies to improve their data security, but overall, the adoption of robust security systems has been relatively slow.
One crucial point to consider is the size and scale of the businesses surveyed. Detailed information on this aspect would provide a more clarified view on the level of risk for companies of different scales. However, regardless of size, it becomes clear that businesses across the board are vulnerable and need to pay more attention to enhancing their data security.
Cyber threat on the rise: A startling 14% increase in unique malware programs: Cybersecurity firm Kaspersky recently reported a disturbing trend in our increasingly digital world. In 2019, their anti-virus tools detected a staggering rise in unique malware programs - over 24 million, a jump of 14% from the previous year.
The term malware refers to an assortment of malicious software, including viruses, worms, and trojans, used by hackers to gain unauthorized access to systems and data. This shocking surge in malware developments paints a troubling picture for internet safety - nearly a fifth of all internet users faced some form of malware attack in 2019.
What does this spike in malware programs mean for you? With more unique programs lurking in the digital sphere, users need to be more proactive than ever to protect their information and systems from malware breaches. This figure is a stark reminder of the ongoing threat of cybercrime and a call to action to secure our digital infrastructure.
As we move forward, it's essential to understand that 'over 24 million' does not merely represent a statistic; it's a sign of the worsening reality of internet security threats. As these risks intensify, we must equip ourselves with fortified anti-virus solutions and a comprehensive awareness of potential cyber threats to navigate the digital world safely.
Why is cybercrime expanding rapidly? The 6 reasons
1. An unprecedented rise in the usage of automation tools for cybercrime
The term 'cyber' has become a staple in virtually every crime involving digital technologies. Identity theft, email phishing, ransomware attacks, are all examples of cybercrimes - a term we hear more often every day. Therefore, it's important we grasp that cybercrimes are not high-tech, futuristic threats, but rather, real offenses committed by hackers using practical and familiar tactics.
Take for example 'phishing'. Even with its strange name, it's just a type of online scam where hackers impersonate a trusted organization to get individuals to reveal their personal information. Another ‘easy tactic’ is the creation of insecure internet architecture. They exploit our increasing reliance on mobile technologies by creating and spreading mobile malware variants. Beyond being simple tactics, these examples illustrate the real-world impact that such crimes can have on individuals and businesses.
Our view on cybercrimes needs to evolve. Rather than seeing them as intricate, mysterious phenomena, we should think about them as commonplace crimes that capitalize on our dependence on digital technologies. Changing our perception in this way allows us to better understand and tackle the issue.
This mindset is not just about redefining terms. It's directly tied to our larger understanding of how and why cybercrime is on the rise. The widespread use of 'cyber' terminology reflects our growing interaction with digital spaces. And as our digital footprints continue to expand, so does the opportunity for cybercriminals. It's crucial that we understand this link so we can be better prepared to navigate the digital world. This is the conversation we need to have when it comes to discussing the expansion of cybercrime and its reasons.
In the wake of the technological revolution, cybercrimes are escalating at an alarming rate. As advanced technologies, particularly Artificial Intelligence (AI) and Machine Learning (ML), become more prevalent, cybercriminals are employing sophisticated methods to carry out their nefarious cyber activities. These technologies bear the brunt of cybercrime's meteoric rise in recent years.
One of the key driving forces behind the acceleration of cybercrime is the availability of automated hacking tools for a minimal price on the dark web. These no longer require hackers to possess advanced technological skills. For instance, tools like exploit kits, remote access trojans (RATs), and botnets are inherent on the dark web. These mechanized tools, designed with AI and ML capabilities, carry out extensive, often devastating, cyber attacks on individuals and organizations alike. They are designed in such a way that even a person with a basic understanding of technology can operate them, thereby escalating the ubiquity and severity of cybercrime.
The unprecedented simplicity of stealing personal information today is another key factor in this alarming development. An illustration of this is social engineering, a potent attack vector where cybercriminals trick individuals into revealing their sensitive data. This could be anything from passwords to bank details, all of which only becomes easier as technology advances and we become more digitally reliant. This is significantly easier and more prevalent than in previous decades and increases the number of potential targets for these cyber criminals.
As the frequency and complexity of these cyberattacks soar, it is crucial to understand how we can safeguard ourselves against them. The use of premium security software, regular software updates, strong and unique passwords, and a basic knowledge of social engineering techniques can significantly decrease one's vulnerability to such attacks.
In an era where our lives are intertwined with technology, the rise in cybercrime is a serious concern, not just for individuals, but also for organizations, financial institutions, and governments around the globe. It's a wake-up call, urging us to heighten our cyber hygiene, enhance national cyber infrastructure, and educate the general public about the risks and protections available. In the face of rapidly advancing cybercrime, such measures are not just a want, but a dire need.
2. An Insight into the Internet's Insecure Architecture
The structure of the Internet is laden with security pitfalls that can be potentially exploited to enable cybercrime. Yet, it's important to understand this in context by outlining vivid instances and comprehensive data. We foresee delving deep into real scenarios and corresponding data will enable you to perceive the intricate correlation between network design and cyber threats.
Moreover, mapping the course of the Internet's evolution is beneficial for the reader to understand why the early stages did not prioritize security. We will walk through the multiple phases of its development, shedding light on the elements that shaped its formation. This historic overview emphasizes on how security took a backseat during those formative years.
Despite the gloomy security landscape, we must focus on the dynamic measures being undertaken to bolster Internet security. We intend to provide insights into the emerging technologies aimed at combating cybercrime and the tangible solutions being worked on. This will infuse optimism in the narrative and reiterate the proactive measures being adopted to counter the challenges. We pledge to substantiate the information with relevant citation and references to uphold our credibility and ensure the accuracy of facts.
In the creation of the Internet's framework, the primary factors taken into account were longevity and stability, with security largely overlooked. The initial architects of our network infrastructure did not prioritize the protection of this transformative technology. Moreover, they failed to anticipate that the Internet would become a medium for transacting immense sums of money and holding information of unrivaled value.
This lack of foresight has resulted in a current Internet landscape that is open to exploitation. A focus on the impacts of this underprepared infrastructure would enhance understanding of the issue. Specifically, elucidating exactly how the Internet’s initial creation without strong security mechanisms has contributed to its current vulnerabilities, and the specific tactics criminals use to exploit these weaknesses, could provide a clearer picture of the situation.
Further context around the architects who underestimated the Internet's explosive growth and key role in modern lifestyle would better connect readers to the content. More relevant and impactful discussions could focus on how these early Internet pioneers possibly didn't foresee the scale and impact the Internet would have.
Furthermore, the communication could be refined for more clarity and conciseness. For instance, the previous statement that "the architects never thought that the Internet would provide a platform for transmitting millions of dollars or information worth a lot more than it is today", could be more succinctly said as, "the architects underestimated the eventual worth of the data and transactions the Internet would accommodate."
Finally, a well-arranged progression of ideas would heighten the piece's readability. Instead of beginning the final thought with "Besides," which can sound informal, saying "Furthermore" presents a more formal alternative that improves the flow of content.
As the Internet transitions from its academic origins to a platform for social interaction and e-commerce, efforts are underway to bolster its security. Yet, the majority of internet architecture continues to rely on insecure data transmission protocols. These deficient standards lack the sufficient encryption necessary to fend off interference or amendments, opening them up to simple exploitation.
Several statistics underscore this vulnerability. For instance, a high proportion of cyberattacks exploiting these frail internet structures are successful. Worse still, these compromises aren't occasional occurrences but alarmingly frequent.
Recent real-world examples further illustrate these threats. Numerous cases have surfaced of cybercriminals taking advantage of insecure structures to carry out their nefarious activities. We're in a high-stakes situation where the security of our digital world dangles precariously.
But let's not just gloss over this with a cold, impersonal tone. We need to feel the urgency here. The stakes could hardly be higher, with our personal data and privacy on the line. And it's not just about us - entire corporations could be brought to their knees, all due to these vulnerable structures.
To better understand the nitty-gritty, let's consider 'hijacked with ease.' Sounds simple enough, doesn't it? The reality, though, is more complex. Faulty encryption, leaked passwords, malware, and more all play their part in compromising our security.
Therefore, while we strive towards enhancing our Internet's security, much remains to be done in tackling its underlying vulnerabilities. All of which supposes, it's clear that the threat of exploitation looms large. The need to act has never been more urgent.
In the evolving digital realm, cybercriminals consistently manipulate the vulnerabilities of certain groups, which include individuals, corporations, and governments, to further their harmful schemes. The internet, indispensable as it is, plays a significant role in controlling our most crucial assets and infrastructures, making it a prime target for these criminals. Especially notable is how the web propels activities such as remote control of utility systems or the operation of key public services, indicating its absolute centrality in our modern world.
However, one cannot overlook the issues tied to the internet's insecurity. Hackers display their cunning by profiting off these security flaws, particularly through activities like phishing, identity theft, or releasing malicious software. These tactics demonstrate the extent of the internet's inherent insecurities, as they wreak havoc in both personal and professional environments.
Moreover, the surge in cybercrime cannot solely be attributed to the internet's insecurity. The rise in mobile malware, the reluctance or delays in adopting robust security measures, and the ever-evolving roles of hackers in breaching data security are contributing factors. By examining these various elements, it becomes clear that addressing cybercrime requires a multifaceted approach that goes beyond merely strengthening internet security.
3. The role of hackers in information security
In today's world, there are individuals who earn a living as professional hackers, also widely recognized as security researchers or ethical hackers. An integral part of their job involves identifying security loopholes in our digital structures and engineering tools to reveal and rectify these weak spots. A significant case that comes to mind is that of a renowned security researcher whose groundbreaking work led to the unearthing of a serious vulnerability in a globally-used software application, subsequently resulting in its repair.
Not to be equated with cybercriminals, ethical hackers play an indispensable role in fortifying our cybersecurity measures. Their work chiefly involves bolstering the internet security infrastructure against malicious hackers by exposing weak points before they can be exploited. Thus, while malicious hackers are intent on causing harm, ethical hackers are our digital defenders who strive to make our cyber experiences safer.
However, it's not all smooth sailing. At times, the tools crafted by these ethical hackers for defense end up in the wrong hands - the hands of those who are intent on causing harm. The repercussions of this can be dire; ranging from minor internet disruption to severe data breaches, disrupting lives and causing immense financial, as well as reputational damage.
Considering these potential threats, it is crucial to examine and implement possible solutions to prevent the misuse of these defense tools. For instance, strict control on the dissemination of these tools or heightened internet regulation are plausible solutions that can reduce the likelihood of these tools falling into the wrong hands.
To break it down, 'enumerating security vulnerabilities' essentially means identifying and listing potential weaknesses in a system’s defenses. This is to ensure that everyone can understand the jobs of these unsung digital heroes - the ethical hackers.
To sum up, ethical hackers play a vital role in cyber safety. Their jobs involve finding system weaknesses and developing tools to fix them. However, when these tools fall into wrong hands, they can cause unwanted disruptions and damage. Hence, it’s crucial to explore preventive solutions to this issue while simplifying complex terminologies for wider understanding.
In our contemporary technologically advanced society, cybercrime is an ever-evolving menace. Both malicious actors and black-hat hackers deftly utilize authentic hacking tools to breach systems, acquiring unauthorized access to confidential information. This appropriation of legal tools for illegal activities has significantly aided the proliferation of cybercrime.
To clearly illustrate this point, let's delve into specific instances of such hacking tools employed by these cyber offenders. For example, black hat hackers often employ legitimate tools like Metasploit or Wireshark, either in their original form or modified for nefarious purposes. These tools, originally designed to assist in ethical hacking, can be manipulated by cybercriminals to exploit system vulnerabilities and delve into unauthorized territories.
Society is currently witnessing a rapid escalation of these hacking tools, a phenomenon we'll refer to as an 'explosion'. The availability and advancements of such tools have significantly impacted the cybersecurity landscape. This explosion has been facilitated by a myriad of factors, including the ubiquitous nature of technology and the exponential growth in the coding community, both professional and rogue.
The direct implications of this tech eruption can be seen in the subsequent race pitting the progression of protective technologies against the advancements of hacking tools. This race is not a trivial issue, but rather a critical determinant in the expansion or containment of cybercrimes. It's a tit for tat scenario: as security technologies strengthen, hackers level up their game with more sophisticated tools, and the cycle continues. The ultimate outcome of this race drastically affects the landscape of information security and, consequently, our online safety.
Aligning directly with the themes explored in this article's summary, the burst in hacking tool development and this ongoing tech race underscore the 'Role of hackers in information security' and validate the 'Slower adoption of strong security' as primary reasons behind escalated cybercrimes. Both these aspects reinforce the importance of not just creating strong security measures but also the need for their quick adoption.
While highlighting the significant role of these online perpetrators in cybercrime, the section offers an insightful perspective on the correlation between technology advancement and cyber threats. Thus, precision, intelligibility, and context remain integral to our collective understanding of such complex scenarios. By addressing these areas, information security is more easily discernible and engaging.
4. Companies are slower in adopting strong security.
In the ever-evolving realm of cybercrime, it is often observed that a multitude of corporations refrain from updating their security infrastructures until the urgency is explicitly highlighted. Generally driven by profit-oriented motivations, organizations tend to postpone the advancement of their security systems until they are targeted by cyberattacks, or their clientele necessitates amplified security. A case in point of such a scenario can be observed in Facebook's approach, where the need for secure sessions wasn't truly comprehended until CEO Mark Zuckerberg's account was targeted by hackers. Thus, it is fair to say that Facebook only started prioritizing user security once it was recognized as a direct issue affecting its operations.
However, this instance merely illustrates a scintilla from the vast cybercrime panorama. The issue of firms being reactive rather than proactive in upgrading security mechanisms spans across various industries - finance, healthcare, retail, and beyond. The factors that instigate a security upgrade are also more diverse. Emerging technologies, international regulatory requirements, industry-specific standards, or reputation management strategies play key roles apart from customer demands or data breaches. Hence, a nuanced examination of triggers for security transformation is paramount.
Moreover, enriching the narrative with hard-hitting facts, figures, or case studies can further accentuate the severity of cybercrime. Quantitative data and real-life examples can attest to the statements and contribute to the reliability of the narrative.
Lastly, it is vital to point out that merely shedding light on the problem will not suffice. The need of the hour is to present comprehensive solutions to address the issue. Guiding readers towards feasible strategies aimed at overcoming this significant hurdle in the digital era is essential. By doing so, the article doesn't just expose the problem, but also steers readers towards potential remedies, marking a significant shift from being problem-oriented to solution-oriented.
Diverse companies implement security measures that are strikingly akin, quite often demonstrating a certain indifference in pinpointing and rectifying potential vulnerabilities in their systems or networks. The pressing need for a thorough scrutiny and prompt resolution of these insecure aspects is often neglected, leaving them susceptible to the threat of cybercriminals. It's imperative to highlight the generally lackluster security practices prevalent within both public and private sectors, which significantly exacerbate the situation. These lax approaches, combined with a reluctance towards the adoption of robust security protocols, serve as primary catalysts to the burgeoning trend of cybercrime.
5. The Increasing Threat to Individuals from Sophisticated Cyber Attacks
The rise of mobile malware variants by an alarming 54% points towards truly advanced cyber attack techniques. This section aims to shed more light on how these cybercriminals specifically target individuals. We dive deep into their cunning methods and strategies, honing in on the types of information most commonly pursued by these criminals. Furthermore, we will explore how individuals, often entirely unknowing, become the biggest victims.
This insight will not only underline significant concerns but also provide proactive advice to the readers, equipping them with the knowledge they need to better protect themselves. Tying in with our overall theme, we'll clarify how the threat to individuals from cyber attacks is not only increasing but evolving in its complexity and sophistication.
Humans have long been considered the most vulnerable aspect of the cybersecurity framework. A significant number of computer users and employees within organizations are not adequately educated on secure practices when using systems. Despite the fact that many users prioritize security and install software tools to identify and eliminate malware, cyber attackers are turning their attention to exploiting human weaknesses.
Delving deeper into the root causes of the escalation in cybercrime, such as the flawed design of internet architecture, the involvement of high-skilled hackers, the sluggish adoption of more robust security measures, the rise in variations of mobile malware, and the continuous aggressive tactics by cybercriminals, will provide an enriched understanding. This connection between human vulnerabilities and the evolving landscape of cybercrime becomes clearer.
Including real-life scenarios or paraphrased case studies tied to these causes will offer a more relatable context for readers, thereby enhancing their comprehension of the topic at hand. Furthermore, some sentences can be rephrased for enhanced clarity. One such instance is the final statement, which can be restructured as, "Therefore, cyber attackers have shifted their focus from merely exploiting system vulnerabilities to taking advantage of human errors". The use of accessible language, devoid of too much technical jargon, is crucial in catering to a diverse readership.
It's a common reality, most cyber attacks bear fruit as a result of unsuspecting individuals being duped into clicking on harmful and fraudulent content such as malicious software or malware, found in website and email attachments. Cybercriminals have perfected the art of manipulation, utilizing strategies such as social engineering to exploit trust, and execute their harmful schemes.
In a rapidly digital world, the rise in cybercrime is profound. A staggering number of individuals have become victims, tricked into divulging critical details such as banking credentials, health records, and personal data, highlighting the necessity of cybersecurity education. To provide a realistic context, let's take as an example the cyber attack realized on Equifax in 2017, where sensitive information of approximately 143 million consumers was accessed unlawfully via a social engineering scheme.
Though the topic of cyber security may seem too technical, it is of utmost importance to each of us. To put it simply, cyber crimes involve, but are not limited to, theft of personal and sensitive data on a large scale to disruptive attacks on websites and internet services. Apart from the global corporations, you and I are equally at risk. We share, knowingly or unknowingly, volumes of personal data online - data that is of high value in the world of cyber criminals.
However, several defensive measures can be adopted to safeguard ourselves from being ensnared in such attacks. It begins with a fundamental awareness, discerning genuine online content from fraudulent ones. Regularly updating your computer and mobile software, setting strong and unique passwords, being cautious of unsolicited online offers and communications are some of the other steps we can follow.
This highlights the need for a more in-depth understanding of advanced cybercrime techniques. Today, Artificial Intelligence (AI) and Machine Learning (ML) have become tools of choice for cyber criminals, with an increasing number of mobile malware variants being identified. By understanding their workings and impacts, we can better prepare ourselves for their potential threats.
Despite the alarming rise in digitized crime, by staying cautious, educated and prepared against increasingly sophisticated techniques, we can help curb the tide of cybercrime.
6. Unpacking the Internet of Things (IoT) Blowout
As we cast the spotlight on the "Internet of Things (IoT) blowout", we must delve into how the dramatic surge of IoT devices has been feeding the cybercrime behemoth. A pivotal aspect to note is that the majority of these devices lack sturdy security foundations, presenting themselves as easy prey for the lurking menace of virtual predators.
Cybercriminals find in these IoT devices a treasure trove of information that they can manipulate or steal for fraudulent purposes. Examples of these devices range from smart home appliances to surveillance cameras, all of which store and process crucial information.
Moreover, it's necessary to understand the ripple effects the IoT has set off within the broader cyber-ecosystem. For instance, the ease of exploiting IoT devices has realigned cybercriminal strategies, drawing more focus on these technology pieces.
So, what can be done to safeguard ourselves and our devices? There are tangible solutions that users and IoT manufacturers can enact to bolster their defense against the cybercrime tide. Discussions surrounding these strategies not only empower users but also create a holistic understanding of the evolving cyber threat landscape.
At a current valuation of $82.4 billion, the global Internet of Things (IoT) market is on an upward trajectory expected to witness a compounded yearly growth rate of 21.3% from 2020 through 2028. IoT devices, notorious for their lacklustre security measures and patching challenges, have the capability to directly connect to the internet and thereby significantly expanding potential attack routes for cybercriminals. The widespread utilization of these IoT systems has been a major factor in the escalating instances of cybercrime, offering a broader playground for hackers.
Each IoT gadget presents a vulnerable point of entry or attack surface. Tech-savvy criminals, bent on system compromises and data theft, exploit these. The end outcome is a burgeoning wave of cyberattacks and relentless malicious campaigns of an unprecedented scale.
With the ever-growing IoT market, the landscape for potential cybercrime threats is only estimated to widen even further. This underlines the pressing need for stronger protective mechanisms. The surge in cybercrime, directly proportional to the expansion of IoT, underscores the importance of robust security measures in the face of evolving technological threats.
In the world of tech industries, Internet of Things (IoT) devices - a term referring to a network of physical objects embedded with software and connectivity - are becoming more and more common. Businesses are embracing these devices due to their potential to boost productivity and optimize key procedures. However, this trend has its downfalls; the staggering number of these 'endpoints' — devices connected to a network— present within any given system makes it an easy target for cybercriminals. Simply put, the more devices there are connected to a network, the higher the chances for a vulnerable device that can be exploited for cyberattacks.
Furthermore, these IoT systems are increasingly controlling vital infrastructure and managing factory operations, drawing the attention of malicious entities. This escalating situation is fueled by a competitive rush among vendors seeking to capitalize on the burgeoning market for IoT devices. As these manufacturers scramble to outperform each other, they often overlook security measures initially, leaving the devices susceptible to exploitation.
So how does this situation tie into the broader context of rising cybercrime? The easy exploitability of IoT devices falls under two main areas. Firstly, the insecure internet architecture makes these devices a soft target for hackers who can easily take advantage of their vulnerabilities. Secondly, the rapid expansion of internet-connected devices is directly proportionate to the increasing rate of cybercrimes. The more connected devices we have, the more opportunities cybercriminals have to strike.
This, however, doesn't mean we have to forsake the positive impacts of IoT on productivity. It calls for a deeper discussion on balancing the benefits and risks. Just as these devices heighten efficiency, their security flaws can bring grave consequences if not properly addressed. Understanding this contrast is vital in appreciating the intricate challenge businesses face when adopting IoT.
But where do we go from here? In light of these threats, efforts need to intensify to address IoT security vulnerabilities. This could involve vendors prioritizing security in the early stages of device manufacture. Also, we need to consider the aftermath of such exploitations. We must ask ourselves, what measures can be taken to mitigate the damage? Starting this conversation is one step towards safeguarding against the relentless wave of malicious campaigns sparked by IoT vulnerabilities.
Effective Measures for Businesses to Secure Their Digital Assets
Proactive security measures form the backbone of any robust cybersecurity strategy. Regularly updating your software to patch vulnerabilities and educating employees on the dangers of phishing attacks are first steps businesses can take to secure their data and systems.
Multi-factor authentication also adds an extra layer of security, making it more difficult for unauthorized persons to gain access to sensitive information. However, businesses should also consider bringing on board cybersecurity professionals to continuously monitor their systems and swiftly address any security breaches that occur.
The formation of a cyber-resilience team is a key move for businesses. This team will constantly evaluate the company's cybersecurity policies to ensure they are not only comprehensive but also current with evolving threats. Proactivity, rather than reactively patching issues as they occur, will lead to a sounder and more successful defense strategy.
Ethical hackers, or 'white hat' hackers, play a vital role in enhancing security measures. Businesses can employ these professionals to identify and rectify weaknesses in their systems before malicious actors manage to exploit them. Addressing the rise in mobile malware also requires attention, and firms must take steps to secure their mobile devices as well.
In conclusion, a strong and resilient security approach is essential in combating the non-stop malicious campaigns initiated by cybercriminals. A balanced, robust security system not only deflects attacks but also meticulously manages them if they do occur. By implementing these tips, businesses can create a safer online environment for their operations, augmenting the overall cyber health of their company and therefore their long-term success.
In today's digital era, businesses are faced with a rapidly growing issue: cybercrime. Taking a proactive approach to security and preventive measures is crucial. Having a well-rounded knowledge about the origins and root causes of internet-based crimes can be immensely helpful. However, it is also deeply relevant to understand the financial implications these crimes desire to businesses. These can encompass a range of factors such as business loss, legal costs, reputation damage, and more. This information is particularly vital to business owners who have the most to lose in such events. Considering the widespread impact of cybercrime not only on individual businesses but also on a societal level is another indispensable aspect that deserves attention and discussion.
In the face of such significant threats, actionable guidance is crucial. This is not just to know why it's essential to be prepared, but how exactly to do so. For instance, investing in more robust security systems or conducting regular security audits with the help of professional hackers can minimize vulnerabilities to a great extent. Taken in conjunction with specific real-life examples or case studies for each cause of cybercrime, this would enable a deeper understanding of the audience.
Finally, the importance of substantiating your points with credible resources and citations cannot be overstated. Not only does it enhance the credibility of your content, but also fosters trust in your audience. Ensuring the facts presented are accurate and reliable helps the reader make informed decisions about their cyber security and ultimately contribute to the global fight against cybercrime.
- Regularly update software: Updating software and operating systems regularly deny cybercriminals the opportunity to exploit vulnerabilities. Patching security flaws make one a less likely target, which is essential to lowering cybercrime.
- Outsource security services: Outsourcing security is the best strategy for small- and medium-sized businesses that lack the resources to strengthen their cybersecurity posture. Managed service providers have access to the latest and most effective security practices, tools, and professionals. Outsourcing security reduces cybercrime significantly.
- Protect against identity theft: Using VPNs in a home or corporate network can help prevent identity theft. It is essential to securely share personal information and passwords to prevent cybercriminals from intercepting the communication.
- Normalize training: Cybersecurity training and awareness should be a common occurrence for businesses and individual computer users. Being conversant with the best security
- Use robust antivirus/antimalware tools: Antivirus software programs enhance cybersecurity since they detect and eliminate harmful programs. Users must ensure to update the antimalware solutions regularly to gain access to the latest threat definitions.
