
What Cybersecurity Threats Are Facing the Upcoming Elections?
In today’s digital age, cybersecurity is paramount in protecting the integrity of upcoming elections. As cyber threats grow more sophisticated, your vote and the democratic
Recent Articles

How to Protect Your Personal Information Online: 5 Tips to Follow
Safeguarding your personal information online is no longer a mere precaution – it’s a necessity. With thousands of cyber-attacks occurring each day, you must ensure

How to Protect Security Cameras Against Hackers
Home security cameras make you and your property safer, right? If yours connect to the internet, they could put you at risk of burglaries and

Legal and Security Foundations of Medicine Delivery App Development
Pharmacy delivery app development has improved healthcare, as patients can now receive essential medications at their doorstep instead of physically visiting pharmacies. However, it is

Unraveling Cybersecurity Challenges in Satellite Communication Systems
In the rapidly evolving landscape of today’s digital communication, a notable technological marvel that stands out is satellite communication systems. Encapsulated in their spacely orbits

Third-Party Breaches on the Rise in Healthcare
Third-party breaches pose one of the biggest challenges in cybersecurity. These attacks occur when hackers compromise a vendor, supplier or other organization associated with the

Bitcoin Price Action on 3-10-24
Bitcoin has shown notable price movement as of March 10, 2024, with its value reaching $68,508, which marks a slight increase from the previous day’s
Need help?
How to Protect Security Cameras Against Hackers
Which Industries Are Most at Risk for Cyberattacks?
Cellphone Locators – Dangers and Malicious Use
Essential Guide to PII Cybersecurity
5 Interesting Cyber Crime Stories
Essential Reading in Cybersecurity
Popular Articles

27 Top Cybersecurity Tools for 2023
We list and describe the top cybersecurity tools that every cybersecurity professional needs to understand. Many companies consider cybersecurity as one of the top priorities.

22 Best Items for a Cybersecurity Checklist
A cybersecurity checklist is important since cybersecurity investments can be a complicated process. An organization must first identify vulnerable assets, determine how vulnerable they are,

The Quick and Dirty History of Cybersecurity
The history of cybersecurity starts in the 1970s. At this time words such as ransomware, spyware, viruses, worms, and logic bombs did not exist. But

23 Top Cybersecurity Frameworks
Many organizations consider cybersecurity to be a priority. The need to implement effective cybersecurity frameworks grows every day. Cybercriminals continuously derive more sophisticated techniques for

Ten Essential Cybersecurity Controls
Cybersecurity controls are essential because hackers constantly innovate smarter ways of executing attacks, aided by technological advancements. In response, organizations have to implement the best

How to Transition to a Cyber Security Career at Any Age
Are you thinking about doing a mid-career transition to a cybersecurity position? It is a great field to join. There are currently millions of unfilled
Stay Connected
CyberExperts
2M+ Followers
@CyberExpertsUS
1M+ Followers
CyberExperts
1M+ Subscribers
Cybersecurity Careers

Top Careers in Cybersecurity and How to Get Started
With the rapid transition into a highly digitized environment, security has become a priority for governments, businesses, and every other organization, resulting in an increased

Mastering the Role of a Cybersecurity Architect
Thre has been an exponential rise in the demand for cybersecurity architects, professionals tasked to develop and implement comprehensive security strategies that protect sensitive data.

Cracking the Code: Does Cybersecurity Require Math?
Does cybersecurity require math? As we delve deeper into the digital age, cybersecurity has become increasingly important in safeguarding our virtual presence against emerging threats.

Best Entry-Level Cyber Security Jobs
In the era of flourishing digital platforms, the role of cybersecurity professionals has never been so critical. As the world grapples with cyber threats, organizations

Highest Paying Cyber Security Jobs
The highest paying cyber security jobs are now more crucial than ever. Those in such positions ensure the safekeeping of sensitive data, networks, and systems

How to Get a Job in Cybersecurity
How to get a job in cybersecurity? With the rise of complex and widespread digital threats, businesses are actively seeking skilled professionals to protect their
Cybersecurity Certifications

Unlocking the IT Security Certificate: A Guide for Tech Enthusiasts
Possessing an IT Security Certificate is no longer an add-on but a defining leverage point in your career trajectory. This multifaceted piece aims to delve

Unlocking Success: ACP-Network Exam Questions-Answers Guide
Introduction to ACP-Network Certification Welcome to the exciting world of ACP-Network certification. In this digital age, where connectivity and data flow like the lifeblood of

Mastering Network Programmability: Exploring the World of Cisco 300-435 Certification
Introduction to Cisco 300-435 Certification The Cisco 300-435 certification is a pivotal milestone in modern networking, offering professionals a unique opportunity to delve into the

10 Most Lucrative IT Certifications in 2023
If you’re interested in the cybersecurity industry and looking for a possible job, getting certified can be a great way to showcase your skills and

7 Easy Steps – How to Become a Cybersecurity Specialist
We outline how to become a cybersecurity specialist and enter a rewarding and exciting career path. Cybersecurity is one of the fastest-growing fields today. As
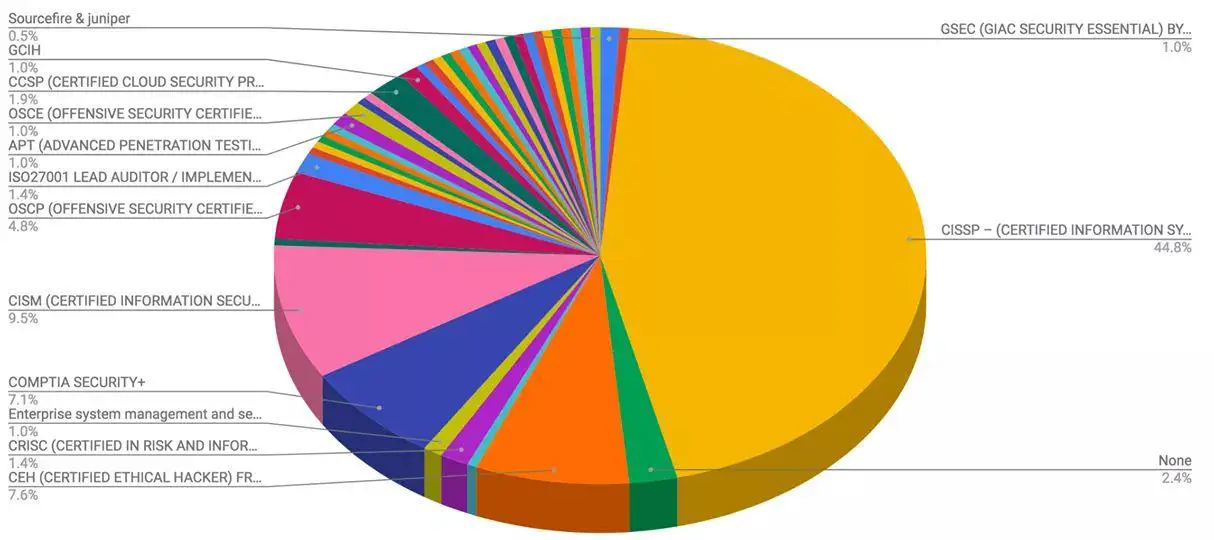
What is the best IT certification to have?
A picture is worth a thousand words. There are a ton of IT certifications but the monster of all certifications is the Certified Information Security